The most important in brief
Beitrag teilen
Reading time 5 minutes
What is a Vulnerability Scanner?
The goal of Vulnerability Scans is that vulnerabilities in the IT infrastructure can be detected at an early stage. The detected vulnerabilities are then prioritised (vulnerability management) and should then also be patched (patch management).
Tools for performing vulnerability scans can simplify this process by automatically finding and even patching vulnerabilities. This can reduce the burden on the IT security team and IT operations.
Scans can be performed by the IT department or via an external service provider.
Typically, the scan compares the details of the target's attack surface against a database. This contains information about known vulnerabilities.
Types of vulnerability scans and vulnerability scanners.
TOP Vulnerability Scanners
1. OpenVAS (Open Source)
The Open Vulnerability Assessment System ([Ext:https://www.openvas.org/|OpenVAS]]) is a vulnerability scanner developed by Greenbone Networks since 2006. It is a vulnerability scanner with a variety of different integrated tests with a web interface for setting up and running vulnerability scans.
Regular updates of the databases take place.
OpenVAS is part of a commercial vulnerability management product family.
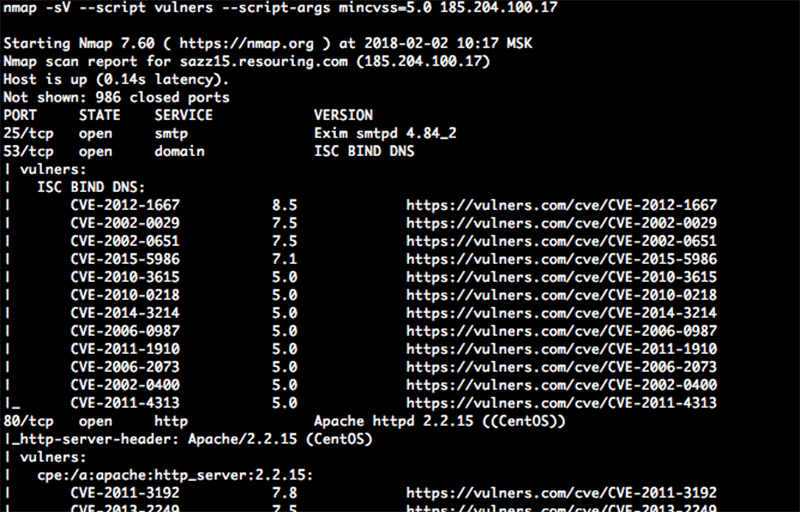
2. Nmap (Open Source)
Nmap, as an abbreviation for Network Mapper, is a free and open source command line tool. Nmap is used for scanning ports, checking for known vulnerabilities and mapping networks. It is a standard tool that is not missing in any Linux distribution. Versions for are also available.
Through its scripting engine (NSE), NMAP is flexible and can not only detect open ports, operating systems and network services, but also perform concrete vulnerability checks.
Nmap has its pre-eminence thanks to the large community of developers and programmers who have been constantly maintaining and developing it since 1997.
Nmap is a port scanner that is popular for penetration testing.
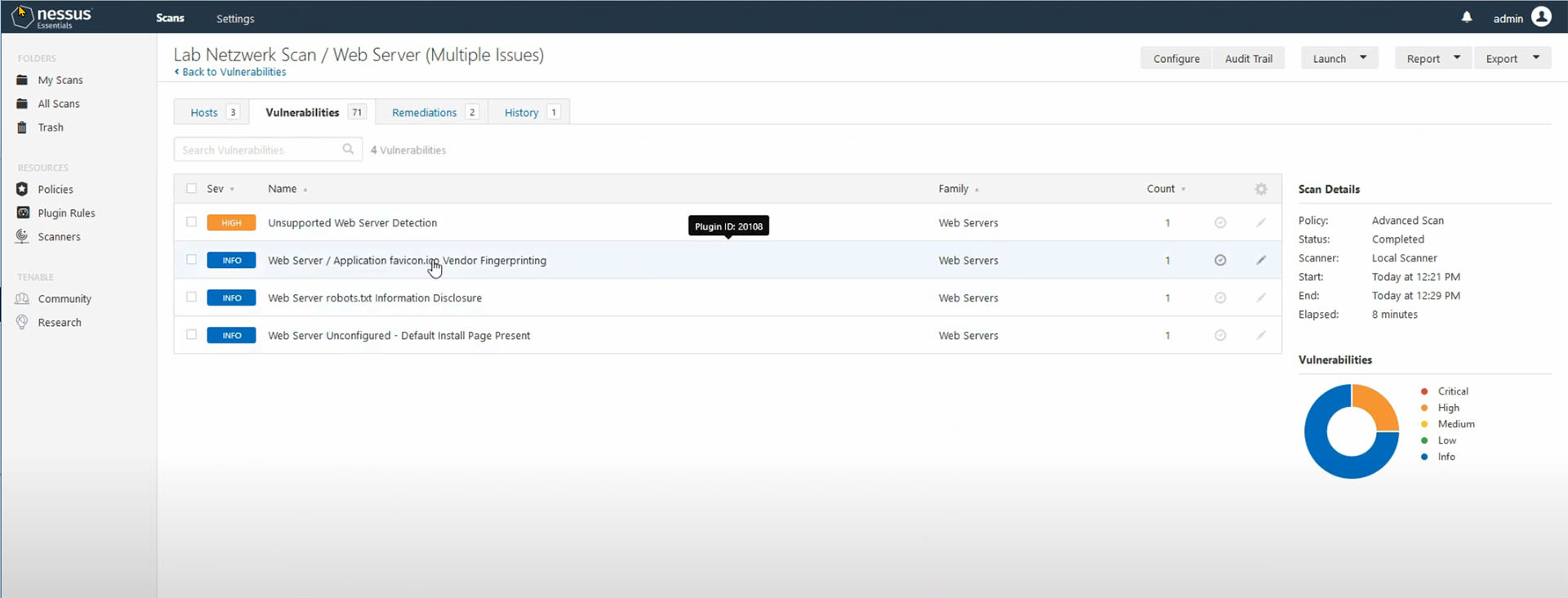
3. Tenable.io Nessus
Nessus is a paid product, but offers some basic tools for free. A cloud solution based on it is available (tenable.io).
However, Nessus offers some features that are not always included in other commercial vulnerability scanners. One of these features is pre-configured scans that meet specific compliance requirements.
The solution is client-server based with a central management instance and scanner agents that can be distributed across the network.
Tenable.io is a cloud solution for vulnerability management and detection based on Nessus.
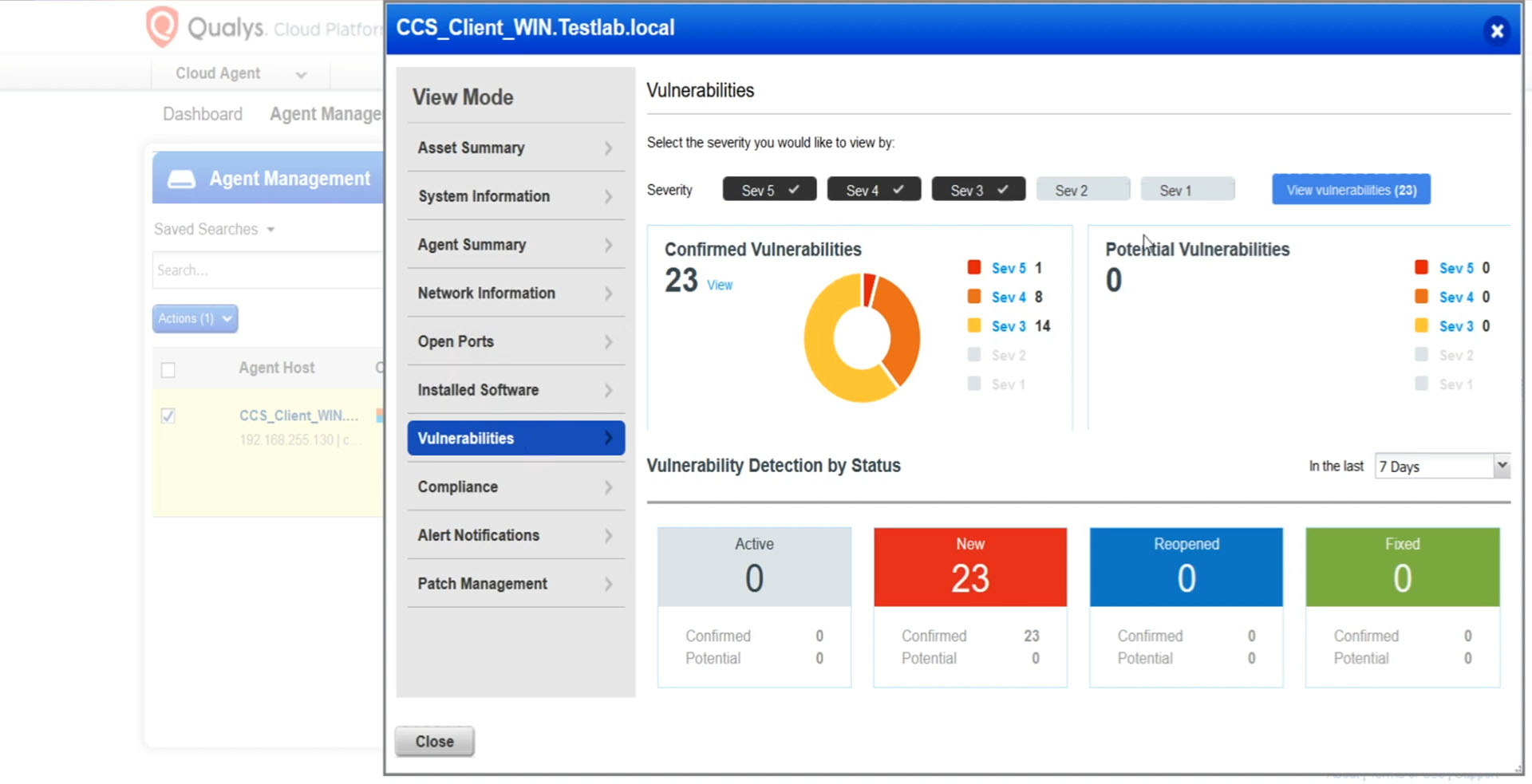
4. Qualys Vulnerability Management Scanner
Qualys is a commercial scanner for network and web application vulnerabilities. The comprehensive solution has powerful components that cover the network, host and web applications.
For example, the Qualys Web Application Scanner attempts to cover these OWSASP top 10 vulnerabilities for web applications, including SQL injection, cross-site scripting (XSS), cross-site request forgery (CSRF).
A limited Community Edition is also available.
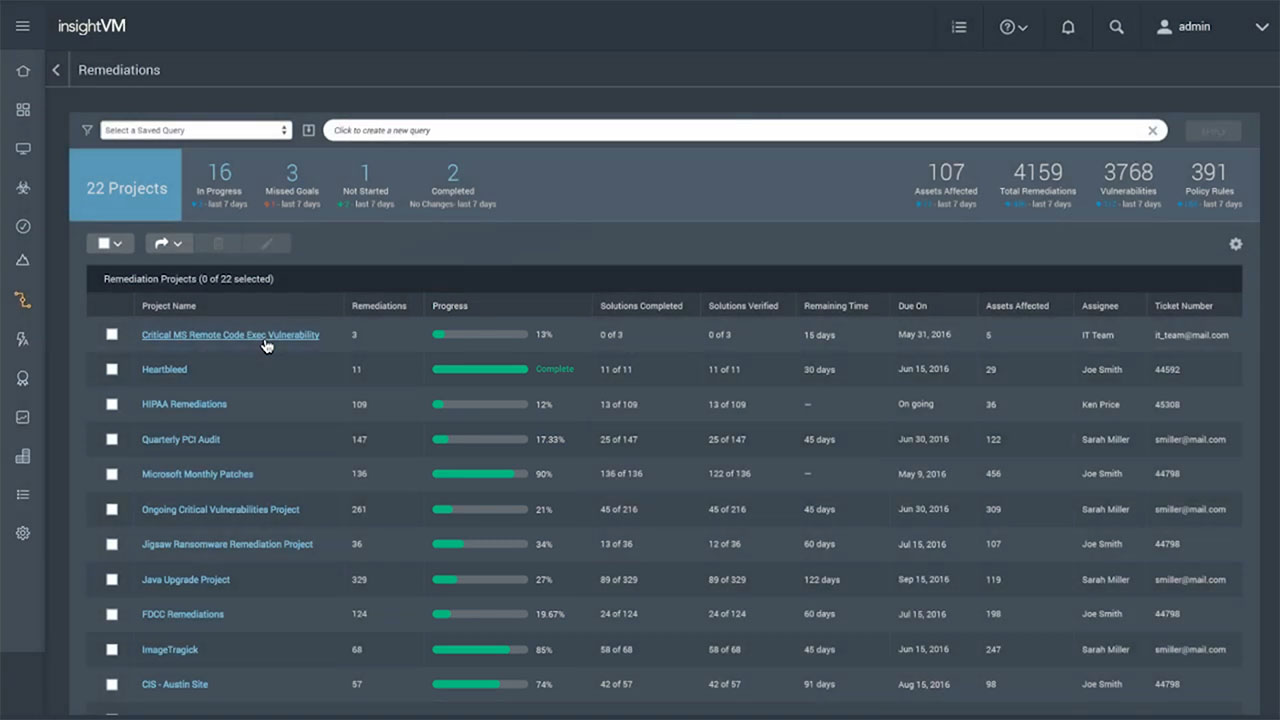
5. Rapid7 InsightVM (formerly Nexpose).
Rapid7 Nexpose is a vulnerability scanner that also supports the vulnerability management lifecycle, including identification, testing, auditing and reporting.
Nexpose is sold as standalone software, as a hardware appliance, as a virtual machine, as a managed service or as a private cloud deployment. User interaction is via a web browser. There is a free but limited community edition as well as commercial versions.
TOP Web Application Vulnerability Scanners
In contrast to the vulnerability scanners listed above, specialised scanners for web applications are designed to accompany the development process.
Many commercial tools like
are used by development teams as part of their DevSecOps processes.
These tools are very comprehensive scanners for web applications that support DAST (Dynamic Application Security Testing) , IAST (Interactive Application Security Testing) and SCA (Software Composition Analysis). These can scan for security issues on websites and in web APIs.
The focus is on the OWASP top 10 as well as the general identification of security problems in web applications such as SQL injections (SQLi) or cross-site scripting (XSS).
The Software Composition Analysis helps to make the "supply chain" of the developed software more visible and can generate a list of the technologies used in the software.
Further scanners
It should be noted that the above lists and examples do not claim to be exhaustive. Nevertheless, in our experience, they cover many of the vulnerability scanners found in practice.
There are now a huge number of service providers who offer their vulnerability scanners online. Often one or more of the tools listed above are technically behind them. These can then be operated via a more or less comfortable web interface.
There are also very many special tools such as Metasploit, Burp Suite, Nikto and others. These are often used as tools in the context of penetration tests or for other special use cases. However, they are not useful as a stand-alone vulnerability scanner.
Frequently asked questions
What are vulnerability scanners?
Vulnerability scanners are software that scans, identifies and assesses networks and network resources for known vulnerabilities. They document all network access points and connected devices and then compare the results of the scans with known vulnerabilities in a database.
What are the key features of vulnerability scanners?
The main features of vulnerability scanning software can be divided into two main groups: identification and correlation and assessment.
What is the difference between identification and correlation?
Vulnerability scanners identify and classify devices, open ports, operating systems and software connected to a network and then correlate this information to the latest known vulnerabilities. They can also detect misconfigurations.
Why are vulnerabilities assessed?
After identifying a vulnerability, these tools also assess and evaluate the level of risk for each vulnerability. They can also perform a root cause analysis to find the cause of the problem. This information informs which vulnerabilities need to be prioritised.
External vs. internal vulnerability scanning.
External scans are performed from outside the network to identify vulnerabilities in servers and applications that are directly accessible via the Internet. Internal scans, on the other hand, identify vulnerabilities that could allow attackers to move laterally on the network.
Authenticated or not - authenticated scanning
Authenticated scans are performed by authenticated users with legitimate credentials. These scans are often more comprehensive than non-authenticated scans because more internal information is available.
Non-authenticated scans do not use credentials. This is because they are only a surface scan. They identify backdoors, expired certificates, unpatched software, weak passwords and poor encryption protocols.
Penetration tests or vulnerability scans?
Penetration tests and vulnerability scans serve similar purposes, but use different methods. Penetration testing is used to actually exploit vulnerabilities. Scanning is used to identify potential vulnerabilities before penetration testing is performed. Logic errors and errors in the area of authentication or authorisation are hardly ever detected by vulnerability scanners.
Inhalt
Releated Content

What is data security? Standards & Technologies
Data security is an important topic for all companies and authorities. Learn more about threats, measures and the legal framework here.
Read more...
Authentication: Differences to authorisation
Authentication and authorization are two words used in IT-Security. They might sound similar but are completely different from each other....
Read more...
Attack Vector and Attack Surface)
An attack vector is a way for attackers to penetrate a network or IT system. Typical attack vectors include ...,
Read more...
Buffer Overflow
A buffer overflow is a programming error that can be exploited by hackers to gain unauthorized access to IT systems. It is one of the best-known...
Read more...
Cybersecurity concept in 8 steps
A cybersecurity security concept refers to guidelines that are intended to ensure IT security in the company. It is about ensuring the availability,...
Read more...
Proxy Server
A proxy server works as an intermediary between two IT systems. Proxy servers offer different functionalities, improved security and optimised data...
Read more...
What is MITRE ATT&CK?
The MITRE ATT&CK Framework is a continuously updated knowledge base consisting of cyber attacker tactics and techniques across the attack lifecycle.
Read more...
Endpoint Security
A proxy server works as an intermediary between two IT systems. Proxy servers offer different functionalities, improved security and optimised data...
Read more...
Need to Know Principle
The need-to-know principle describes a security objective for confidential information. Access should only be granted to a user if the information is...
Read more...
NTLM Authentication
In this article, we explain what NTLM authentication is, how it works, and how it can be exploited by attackers.
Read more...
Information Security Management Systems (ISMS)
An Information Security Management System (ISMS) defines methods to ensure information security in an organisation.
Read more...
CVSS (Common Vulnerability Scoring System)
The CVSS Score provides a numerical representation (0.0 to 10.0) of the severity of a security vulnerability in IT. We explain how the Common...
Read more...
What is Information Security?
Information security is intended to ensure the confidentiality, integrity and availability of information. The information can be available on IT...
Read more...
CIS Controls - A Quick Overview of CIS Controls
The CIS Critical Security Controls (CIS Controls) are a prioritized list of protective measures to defend against the most common cyber attacks on IT...
Read more...
Penetration Tester Career Guide
How does one actually become a pentester? What does a pentester earn? Do career changers also have a chance? And what does a penetration tester do all...
Read more...
Firewalls & Firewall-Architecture
How does a firewall actually work? What does a good enterprise firewall architecture look like? To what extent does appropriate network segmentation...
Read more...Have we sparked your interest?
Just give us a call or write us a message!