CVSS in a nutshell
Beitrag teilen
Reading time 11 minutes
1. the CVSS (Common Vulnerability Scoring System)
CVSS v3.1 Calculator (CVSS Score)
What is the CVSS (Common Vulnerability Scoring System)?
The Common Vulnerability Scoring System (CVSS) is a standard for assessing IT security vulnerabilities. The CVSS score is a numerical representation of the severity (0-10) of a security vulnerability. CVSS scores are used to compare and prioritise the remediation of IT vulnerabilities. Vulnerabilities with a high CVSS score are prioritised over vulnerabilities with a low CVSS score.
Although assessing IT vulnerabilities with a standardised methodology and uniform scoring is very beneficial for information sharing, the limitations of CVSS should also be known to ensure appropriate use.
Initial research by a US Department of Homeland Security working group led to the release of CVSS 1.0 in February 2005, and since then CVSS has been maintained by the Forum of Incident Response and Security Teams (FIRST), a US-based non-profit organisation. As of 2019, the latest version is.
CVSS Score
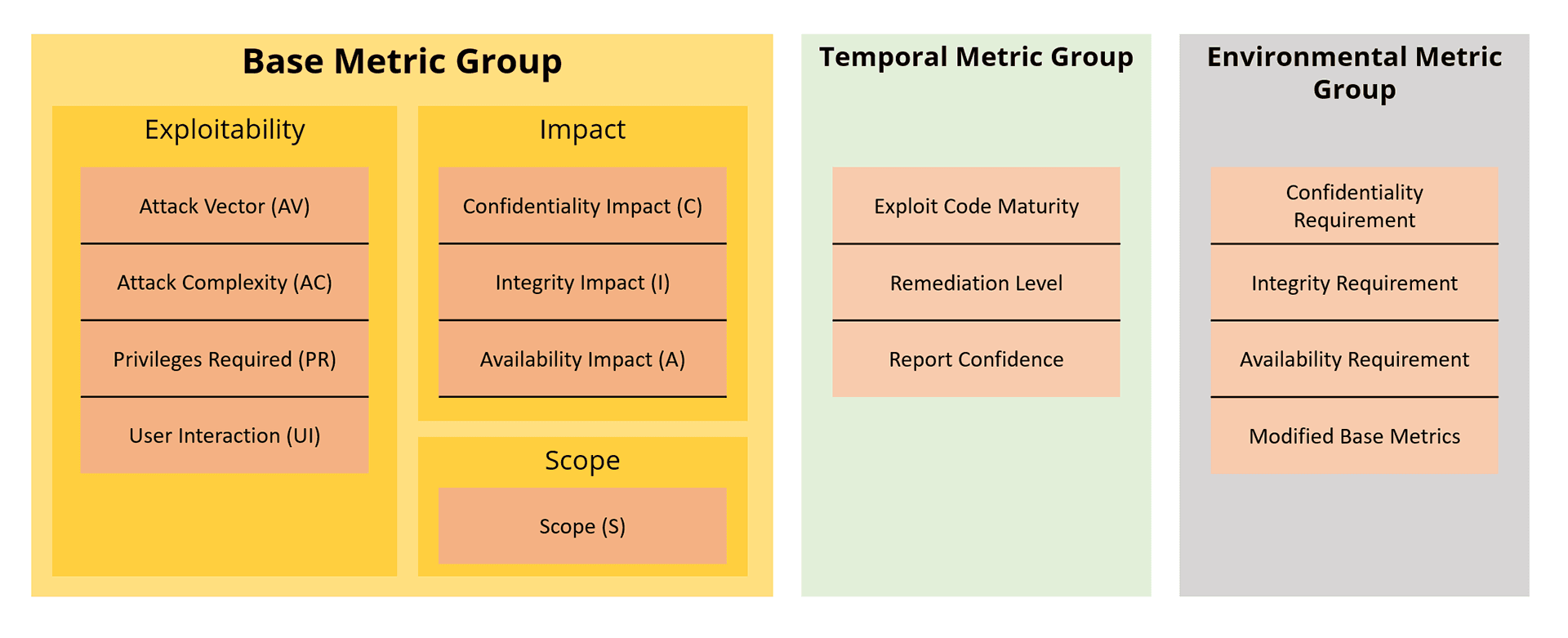
A CVSS score is composed of up to three individual assessments (Base, Temporal, Environmental). The central assessment is that of the base metrics. The result of the base evaluation is the CVSS base score and can then be adapted to the own IT environment by adding temporal or environmental factors. In practice, however, the term CVSS score is often simply understood to mean the CVSS base score.
CVSS Vector
A CVSS score can also be specified as a so-called CVSS Vector. This is a shortened text format from which the CVSS Score can be derived.
2. Definition of CVSS Score
In IT security, the use of CVSS scores to measure the criticality of an IT security vulnerability is the de facto standard. They are also commonly used in penetration testing to assess the vulnerabilities discovered.
CVSS scores are also the most important metric for managing security vulnerabilities in the IT infrastructure and prioritising their closure.
A CVSS score can consist of up to three individual evaluations, so-called metric groups. The result is a CVSS Basic Score, an optional CVSS Temporal Score (time-dependent) and a CVSS Environmental Score (depending on the specific IT environment).
- Base: The Base metric shows the attributes inherent to a vulnerability that are independent of the environment or time. The result of the assessment is the CVSS Base Score.
- Temporal: The temporal metric takes the base metric as a starting point and decreases it somewhat based on some considerations such as: If there is no well-functioning and published exploit code, the CVSS Score is slightly lowered. If there is a temporary fix/workaround, the CVSS score is slightly decreased. The result is then the CVSS Temporal Score.
- Environmental: The environmental metric can either increase or decrease the CVSS Score based on considerations such as the particular vulnerability/criticality of the affected data or a change in vulnerability due to a specific system configuration or network constellation. The result is the CVSS Environmental Score.
Qualitative scale of the CVSS Score
Sometimes it is useful to have a descriptive representation of the numerical scores. For this purpose, the following scheme is included in the standard since CVSS v3.0.
| Vulnerability Severity | CVSS Base Score |
|---|---|
| None | 0.0 |
| Low | 0.1 - 3.9 |
| Medium | 4.0 - 6.9 |
| High | 7.0 - 8.9 |
| Critical | 9.0 - 10.0 |
For example, a CVSS base score of 6.0 has a severity rating of Medium."
Example (EternalBlue)
EternalBlue is the name of an exploit that exploits programming errors in the SMB implementation of Windows. The vulnerability is known as CVE-2017-0144 (SMB Remote Windows Kernel Pool Corruption). If a Windows system was vulnerable, it could be used to remotely gain administrative privileges on the compromised system.
CVSS Basic Score: 8.1 (HIGH).
CVSS Vector: CVSS:3.1/AV:N/AC:H/PR:N/UI:N/S:U/C:H/I:H/A:H
3. Operationalisation of CVSS scores
The published CVSS scores of IT vulnerabilities are usually the CVSS base scores. The starting point is what damage can be done with an IT vulnerability.
The more important question in companies and authorities, however, is actually whether this IT vulnerability can cause damage here specifically in this environment and currently.
Therefore, the temporal and environmental factors should be included in an assessment and thus also prioritisation. When operating one's own vulnerability management programme, such considerations are essential to ensure correct prioritisation.
Nevertheless, I would like to point out that there is basically (almost) no legitimate reason not to patch vulnerabilities promptly and also not to keep software up-to-date - but this is another discussion.
4. CVSS Base Score (CVSS Basis Score)
Since the base metric group focuses on the core properties of an IT vulnerability, it does not change over time or depending on environmental factors.
When a CVSS score is documented for a vulnerability in a public system such as NIST's National Vulnerability Database NVD, the score given is almost always the CVSS Base Score.
To calculate the CVSS Base Score (also CVSS Basis Score), the following factors are evaluated:
Vulnerability (Exploitability) rating
The exploitability rating refers specifically to the IT vulnerability without relating it to a particular configuration or other compensating factors. This assessment has four components - attack vector (AV), attack complexity (AC), required privileges (PR) and whether user interaction (UI) is necessary.
Attack Vector (AV)
The attack vector is an indicator of the level of access an attacker needs to exploit the vulnerability. A vulnerability that requires local or even physical access to a target system is much more difficult to exploit than one that can be exploited remotely purely over the network or even the Internet.
The attack vector is evaluated according to the following scheme:
Complexity of attack (AC).
This Complexity of Attack represents conditions outside the attacker's control that must be present for the vulnerability to be exploited. Most often, this is a specific required configuration of the target system.
Attack complexity is rated as either low or high:
Required Privileges (PR).
Required Privileges describes the level of privileges or necessary access an attacker must have for a successful attack.
Required privileges can be divided into three levels:
User interaction (UI)
The User Interaction describes whether another user must do something for a successful exploit of the vulnerability to occur.
The necessity of a user interaction is evaluated as follows:
Scoring the impact of a vulnerability (Impact).
Impact metrics are intended to evaluate the consequences of the exploitation of an IT vulnerability on the information security protection objectives (confidentiality, integrity, availability). In other words: What is the negative end result as a consequence of a successful attack?
Confidentiality (C)
Confidentiality refers to the disclosure of sensitive information to unauthorised persons.
The loss of confidentiality is rated as follows:
Integrity (I)
Integrity refers to whether the protected information has been manipulated or altered in any way. If there is no way for an attacker to alter the accuracy or completeness of the information, integrity is maintained.
The loss of integrity is thereby assessed as follows:
Availability (A)
If information is no longer available in a timely manner due to an attack, for example due to deletion/encryption (ransomware) or a DDOS attack, the availability is negatively affected.
The loss of availability is assessed as follows:
Scope (S)
The Scope is used to determine whether an IT vulnerability in one system or component can have an impact on another system or component that lies outside the security instance of the attacked component.
The term security instance refers to mechanisms that are responsible for access control. This can be, for example, applications, the operating system, a container, a virtual machine, a browser sandbox or similar.
So if a security vulnerability in a browser leads to an attacker being able to read out the browser history, this usually does not count as a change in scope.
If, on the other hand, a browser vulnerability leads to data being accessed at the operating system level, it does. From the browser's perspective, the operating system is not part of the browser's security instance.
The scope can be evaluated as follows:
5. CVSS Temporal Score (time-dependent)
With the CVSS Temporal Score, the effects of an IT security vulnerability can be evaluated over time. The basis of the temporal score is the CVSS Basic Score.
The basic idea is the current exploitability of the vulnerability and the possibility of countermeasures, such as an existing security patch.
Exploit Code Maturity: As long as there is no method to exploit a vulnerability, it is harmless. As with most software, the code available to exploit a vulnerability may mature over time, becoming more stable and more widespread. As this happens, the score for that subcomponent increases.
State of Mitigation (Mitigation Status): When a vulnerability is first discovered, there may be no patch or other mitigation available. Over time, workarounds, temporary fixes, and eventually official patches become available, causing the vulnerability score to decrease as remediation improves.
Report Confidence: Confidence measures the degree of validation showing that a vulnerability is both real and exploitable.
6. CVSS Environmental Score (environment-dependent).
CVSS environmental metrics allow the base CVSS to be modified based on custom security requirements and environmental criteria.
Environmental security requirements: The security requirements provide information for the criticality of the information involved. Mission critical data receives a higher rating than less critical data. For example, a vulnerability in an application running in a compartmentalised virtual machine would receive a lower score than if the same application were running on a mission critical server with important customer data.
Change in baseline metrics: The values of the baseline CVSS metrics may change due to remediation actions. For example, if a server is physically disconnected from the network, a vulnerability exploitable through the network may no longer matter.
Frequently asked questions
Development of the Common Vulnerability Scoring System (CVSS)
Research by a working group of the US Department of the Interior and Homeland Security led to the release of CVSS 1.0 in February 2005, and since then it has been further developed by the Forum of Incident Response and Security Teams (FIRST), a US non-profit organisation. As of 2019, the current version 3.1 has been released.
Feedback from users of CVSS 1.0 indicated that there were significant problems with the first draft of CVSS in practice. Work on CVSS version 2.0 began in 2005, and the final specification was published in June 2007. CVSS version 3.0 followed in 2015, and the current version is CVSS 3.1, released in 2019.
Research by a US Department of Homeland Security working group led to the release of CVSS 1.0 in February 2005. Since then, it has been maintained by the Forum of Incident Response and Security Teams (FIRST), a US-based non-profit organisation.
Feedback from users of CVSS 1.0 indicated that there were significant problems with the first draft of CVSS in practical use. Work on CVSS version 2.0 began in 2005, and the final specification was published in June 2007. This was followed by CVSS version 3.0 in 2015, and the current version is CVSS 3.1, released in 2019.
What is the difference between CVSS and CVE?
CVE stands for Common Vulnerability Enumeration and is a unique identifier for each vulnerability listed in the NIST NVD. The CVSS score gives an indication of the severity of each CVE. However, the CVSS Score is not included in the CVE list. However, the NVD contains the necessary information on this.
A CVE is indicated as follows: CVE-[4-digit year]-[sequential number].
For example, the for the vulnerability known as Eternal Blue is CVE-2017-0144.
The CVSS score of Eternal Blue is given as 8.1 (high) in the NVD.
What is the CVSS base score?
CVSS scores are the primary metric used to compare one IT vulnerability to another in order to determine priorities and criticality. A CVSS score always consists of a base score and two optional scores (temporal and environmental).
The base score represents the invariant properties of the vulnerability itself.
How is the CVSS score calculated?
The calculation formula for the case scope "unchanged" is defined as follows:
ISS = 1 - [ (1 - Confidentiality) × (1 - Integrity) × (1 - Availability) ]
IMPACT = 6.42 × ISS
EXPLOITABILITY = 8.22 × AttackVector × AttackComplexity × PrivilegesRequired × UserInteraction
SCORE = Roundup (Minimum [(Impact + Exploitability), 10])
Details of the individual ratings can be found in the CVSS 3.1 Specification Document, Chapter 7.
CVSSv2 vs. CVSSv3?
CVSS is currently available in version 3.1. Version 3 was intended to address some of the shortcomings of the previous version v2.
The assessment of concrete IT security vulnerabilities differs between v2 and v3, sometimes considerably. In particular, v3 takes into account the permissions required for the exploitation of a vulnerability as well as the ability of an attacker to spread after the exploitation of a vulnerability.
Inhalt
Releated Content

What is data security? Standards & Technologies
Data security is an important topic for all companies and authorities. Learn more about threats, measures and the legal framework here.
Read more...
Authentication: Differences to authorisation
Authentication and authorization are two words used in IT-Security. They might sound similar but are completely different from each other....
Read more...
Attack Vector and Attack Surface)
An attack vector is a way for attackers to penetrate a network or IT system. Typical attack vectors include ...,
Read more...
Buffer Overflow
A buffer overflow is a programming error that can be exploited by hackers to gain unauthorized access to IT systems. It is one of the best-known...
Read more...
Cybersecurity concept in 8 steps
A cybersecurity security concept refers to guidelines that are intended to ensure IT security in the company. It is about ensuring the availability,...
Read more...
Proxy Server
A proxy server works as an intermediary between two IT systems. Proxy servers offer different functionalities, improved security and optimised data...
Read more...
What is MITRE ATT&CK?
The MITRE ATT&CK Framework is a continuously updated knowledge base consisting of cyber attacker tactics and techniques across the attack lifecycle.
Read more...
Endpoint Security
A proxy server works as an intermediary between two IT systems. Proxy servers offer different functionalities, improved security and optimised data...
Read more...
Need to Know Principle
The need-to-know principle describes a security objective for confidential information. Access should only be granted to a user if the information is...
Read more...
Top 10 Vulnerability Scanners for 2025
Vulnerability scanners are automated tools that organisations can use to monitor their networks, systems and applications for security weaknesses....
Read more...
NTLM Authentication
In this article, we explain what NTLM authentication is, how it works, and how it can be exploited by attackers.
Read more...
Information Security Management Systems (ISMS)
An Information Security Management System (ISMS) defines methods to ensure information security in an organisation.
Read more...
What is Information Security?
Information security is intended to ensure the confidentiality, integrity and availability of information. The information can be available on IT...
Read more...
CIS Controls - A Quick Overview of CIS Controls
The CIS Critical Security Controls (CIS Controls) are a prioritized list of protective measures to defend against the most common cyber attacks on IT...
Read more...
Penetration Tester Career Guide
How does one actually become a pentester? What does a pentester earn? Do career changers also have a chance? And what does a penetration tester do all...
Read more...
Firewalls & Firewall-Architecture
How does a firewall actually work? What does a good enterprise firewall architecture look like? To what extent does appropriate network segmentation...
Read more...Have we sparked your interest?
Just give us a call or write us a message!