Data Security in a nutshell
Beitrag teilen
Reading time 8 minutes
1 What is data security?
Data security is understood to mean the appropriate protection of data, regardless of whether it is personal or not. Data security is intended to protect not only data such as technical specifications, company secrets or source code, but also analog data such as printed documents and also personal data.
Companies and public authorities can take a number of measures to ensure that analog and digital data is protected from threats. The protective measures themselves can be either organizational or technical.
2 What are the goals of data security?
The most important goals of data security are to protect data of all kinds from threats - from loss to manipulation to deletion of this data. This is to achieve the three most important protection goals - confidentiality, integrity, and availability.
3 What laws and legal requirements are there for data security?
Companies in Germany and Europe are legally obligated to implement appropriate risk management and, consequently, to establish regulations for dealing with IT risks. This section lists and comments on the most important legal regulations and standards for corporate IT.
In addition to legal requirements, there are also security standards such as ISO 27001 or TISAX. They all aim to help companies and public authorities reduce the risks of data processing to an acceptable level.
Basic Data Protection Regulation and Federal Data Protection Act
The General Data Protection Regulation (GDPR) is an EU regulation and applies directly in every EU member state. It does not require implementation in national law. The GDPR sets out rights, obligations and measures for protecting personal data.
The updated German Federal Data Protection Act (BDSG) has been in force since 25.05.2018 and since then only supplements the DSGVO. The DSGVO and the BDSG are to be applied together.
IT Security Act
The amended IT Security Act (IT-Sig 2.0) has been in force since May 2021. It significantly expands the regulations for operators of critical infrastructures (KRITIS).
Among the new features are the mandatory use of attack detection systems from May 2023, extended reporting obligations in the event of malfunctions, and mandatory notification of security-critical critical components.
critical infrastructures include operators above a specified minimum size in industries such as energy and water supply, healthcare, finance, or IT and telecommunications.
Act on Control and Transparency in the Corporate Sector
In 1998, the German Act on Corporate Control and Transparency (KonTraG) amended the content of the German Commercial Code (HGB), the German Limited Liability Companies Act (GmbHG), and the German Stock Corporation Act (AktG) to establish clear management responsibility for IT security.
Only if all the required measures for IT security and IT risk management are demonstrably implemented can the management escape its responsibility.
Further legal regulations
There are several other legal frameworks and legal texts that have an effect in the IT environment.
It should be noted that the preceding list is intended only as a guide and cannot replace legal advice.
4 What are the threats to data security?
The threats to enterprise data security are as varied as the potential consequences. Let's illustrate with some practical examples.
Ransomware cyber attack.
Cyber criminals try to penetrate an organization's IT environment through phishing or other social engineering techniques, bringing malware we ransomware to execute. Ransomware is primarily an availability attack.
Unprotected use of USB sticks
The unprotected use of USB sticks can introduce malware into the company as well as cause data to flow out of the company in an uncontrolled manner.
Loss of company laptops
If a company laptop is lost, there is always a risk that company data, personal data, VPN access information, passwords or the like will fall into unauthorized hands.
Unprotected company network
Employees bring their own devices and connect them to the company network. Depending on the configuration of the network, this can pose a massive IT security problem.
Fire at the site
A fire at a company site can cause a massive data availability problem.
5 How do data security and data protection differ?
While data security is primarily concerned with the general technical protection of data, data protection aims to protect a very specific type of data, namely personal data.
Data security aims to protect all corporate data, with no restrictions on the type of data.
Personal data must not only be technically protected and thus kept secure, but its collection, processing, and disclosure must also be restricted.
The difference between data security and data protection becomes particularly clear when they are incompatible. Cloud services are often questionable from the point of view of data protection because the use by external providers can no longer be traced and controlled.
In contrast, the use of cloud-based services can have a positive impact on data security. With their economies of scale, cloud providers are often able to take IT security measures that are not feasible for SMEs in this way. Extensive data protection measures (backups) are also frequently part of the offers.
6 Which measures increase data security?
Even if there is no "golden package" that offers guaranteed protection against threats, a number of measures can be derived that offer very good protection against the most dangerous cyber attacks.
Such a package of measures includes technical and organizational measures. For this purpose, the Center of Internet Security (CIS) publishes and updates a list of critical security measures that can defend against almost all attacks that occur in practice. This list comprises three stages of expansion. Below, I list the basic measures from it that should be implemented by every company - also for data protection reasons.
My recommendation is that you critically compare the measures already implemented with the list below. If measures from it have not yet been established at all, this should be addressed as soon as possible.
Basic
- Security Awareness: Introduce a training concept to train employees in handling sensitive data and IT systems. Training should occur at the time of hire and at least once a year. Handling social engineering attacks, secure authentication procedures, and sensitive data should be included.
- Security Incident Handling: Designate at least one person to handle security incidents. If you are working with an external provider, define an internal person who is responsible for reconciliation. Also, be clear on how to report potential security incidents.
- Service providers: Create a list of the service providers and cloud services you use with key contacts and what type of data may be transferred.
- Rules for working from home: Introduce frameworks for working from home (security policies, company laptop, VPN, 2FA, etc.).
- Secure workspaces with access control: Implement secure workspaces for own employees with access control.
Management of IT systems
- List of IT systems: Create a list of all shared IT systems such as user clients, servers, network devices, IoT devices, etc.
- Remove non-shared devices from the network: Periodically check for and remove non-shared devices connected to your network.
- Use encryption: Encrypt all user clients, especially all laptops and mobile devices. Similarly, websites should only be available via HTTPS.
- Host-based firewall: Use a host-based firewall with a default-deny-all rule - if implementable also in the internal network.
- Anti-malware: Install an anti-malware solution on all network devices. Configure automatic updates for this software.
Data management
- Data inventory: Create a list of sensitive data.
- Manage access to sensitive data: Ensure that sensitive data is accessed only after clearance and on a need-to-know basis.
- Secure deletion of data: Ensure that there is an effective process for deleting data that is no longer needed.
- Backups: Regular automatic backup of data to a secured, isolated environment ensures that damage is limited in the event of potential data loss. Regular testing for recovery is also strongly advised.
Applications & Software
- Software Inventory: Create a list of approved software within the organization.
- Security patch availability: Ensure that all approved software (including operating systems, browsers, and email clients) is patched and updated by the vendor.
- Secure configuration: All IT systems should be configured to be equally secure in a standardized manner.
- Vulnerability management: A process for identifying, prioritizing and promptly closing all vulnerabilities should be established.
- Automated patching: If possible, operating systems and other software should be patched automatically.
Management of the network
- Logging: Determine whether event logs should be collected on the systems themselves or centrally with a log management system. Ensure that all relevant events are logged.
- DNS filtering: Deploy a DNS filtering solution that blocks access to known malicious domains.
User management and access by users
- User account inventory: An overview of all users should be maintained. If an employee leaves,
- Automatic Logout: After a few minutes of inactivity, you should lock all user sessions. For Windows, the screen saver should activate after 3-5 minutes.
- Two-factor authentication: Two-factor authentication must be enabled for administrative activities and external access to the network and all applications accessible via the Internet. Biometric systems such as Windows Hello are also an option when used securely with SSO.
- Password length: Password length should be 14 characters or more. With 2FA, 8 characters is sufficient for a PIN.
- Separation of administrative accounts: Administrative accounts and user accounts must be separated. This often results in system administrators having two or more accounts: A user account and one or more administrative accounts.
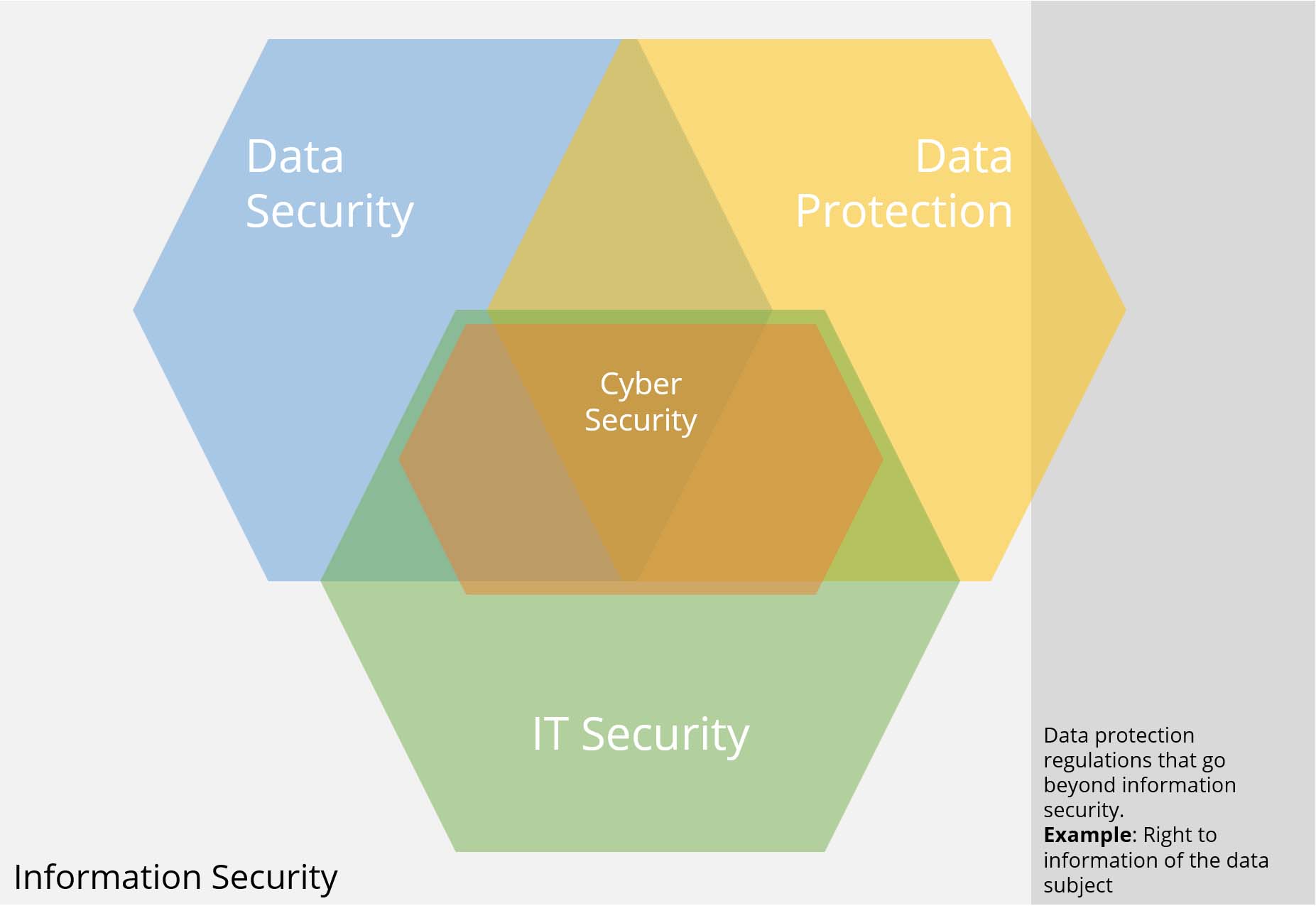
7 Data Security vs Information Security vs Cybersecurity.
To be honest, some of the terms are interchangeable in practice. Thus, an exact delineation and a clear definition of the terms is difficult, as they are interpreted differently depending on context and author. Nevertheless, the following delimitation should provide some orientation:
| Term | Description |
|---|---|
| Data security | Data security is intended to ensure the three protection goals of confidentiality, integrity and availability of data through technical and organizational measures. The term data often includes analog data, more rarely, but broader concepts such as 'the spoken word'. The term data is often used in a regulatory context, for example in the BDSG. |
| Data protection | Data protection refers to the protection and control of personal data as significantly prescribed by laws such as the BDSG and the DSGVO. |
| Information security | Information security is intended to ensure the three protection goals through technical and organizational measures for information. Information security always deals with all information, regardless of the information carrier. The term information is commonly used in security standards such as ISO 27001 or IT-Grundschutz. |
| IT security | IT security aims to implement the three protection goals for the context of information technology. |
| Cybersecurity | Cybersecurity wants to maintain IT security against attacks from the Internet. Especially in the environment of public authorities and in the Anglo-American language area, however, IT security and cyber security are equated |
Inhalt
Releated Content
Authentication: Differences to authorisation
Authentication and authorization are two words used in IT-Security. They might sound similar but are completely different from each other....
Read more...
Attack Vector and Attack Surface)
An attack vector is a way for attackers to penetrate a network or IT system. Typical attack vectors include ...,
Read more...
Buffer Overflow
A buffer overflow is a programming error that can be exploited by hackers to gain unauthorized access to IT systems. It is one of the best-known...
Read more...
Cybersecurity concept in 8 steps
A cybersecurity security concept refers to guidelines that are intended to ensure IT security in the company. It is about ensuring the availability,...
Read more...
Proxy Server
A proxy server works as an intermediary between two IT systems. Proxy servers offer different functionalities, improved security and optimised data...
Read more...
What is MITRE ATT&CK?
The MITRE ATT&CK Framework is a continuously updated knowledge base consisting of cyber attacker tactics and techniques across the attack lifecycle.
Read more...
Endpoint Security
A proxy server works as an intermediary between two IT systems. Proxy servers offer different functionalities, improved security and optimised data...
Read more...
Need to Know Principle
The need-to-know principle describes a security objective for confidential information. Access should only be granted to a user if the information is...
Read more...
Top 10 Vulnerability Scanners for 2025
Vulnerability scanners are automated tools that organisations can use to monitor their networks, systems and applications for security weaknesses....
Read more...
NTLM Authentication
In this article, we explain what NTLM authentication is, how it works, and how it can be exploited by attackers.
Read more...
Information Security Management Systems (ISMS)
An Information Security Management System (ISMS) defines methods to ensure information security in an organisation.
Read more...
CVSS (Common Vulnerability Scoring System)
The CVSS Score provides a numerical representation (0.0 to 10.0) of the severity of a security vulnerability in IT. We explain how the Common...
Read more...
What is Information Security?
Information security is intended to ensure the confidentiality, integrity and availability of information. The information can be available on IT...
Read more...
CIS Controls - A Quick Overview of CIS Controls
The CIS Critical Security Controls (CIS Controls) are a prioritized list of protective measures to defend against the most common cyber attacks on IT...
Read more...
Penetration Tester Career Guide
How does one actually become a pentester? What does a pentester earn? Do career changers also have a chance? And what does a penetration tester do all...
Read more...
Firewalls & Firewall-Architecture
How does a firewall actually work? What does a good enterprise firewall architecture look like? To what extent does appropriate network segmentation...
Read more...Have we sparked your interest?
Just give us a call or write us a message!