The most important facts in brief
Beitrag teilen
Reading time 6 minutes
What is the MITRE ATT&CK®?
MITRE ATT&CK® (Adversarial Tactics, Techniques, and Common Knowledge) was developed in 2013 by MITRE Corporation to document attacker tactics and techniques based on real-world observations.
In doing so, researchers wanted to study the behaviour of attackers and defenders to improve detection after compromise.
The resulting ATT&CK framework is a knowledge base of cyber-criminal and cyber-attacker behaviours that reflects the different phases of the attack lifecycle.
The abstraction into concrete tactics, techniques and sub-techniques provide an easily understandable level of abstraction on which different IT security teams can communicate with each other.
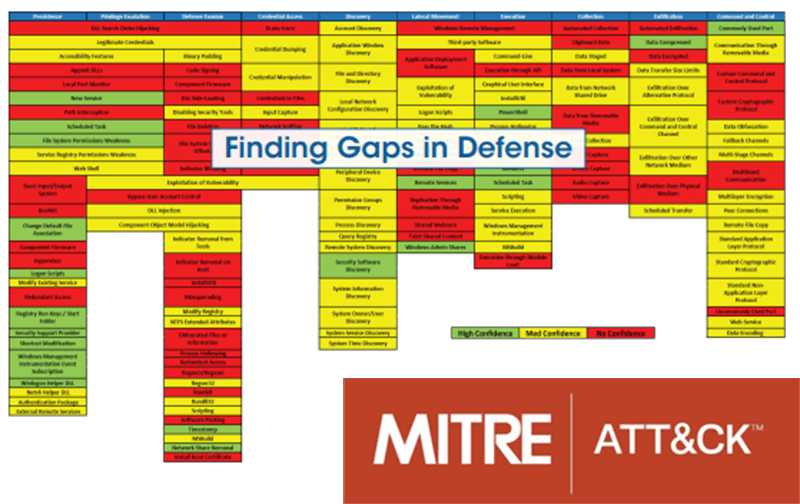
MITRE represents ATT&CK in the form of a matrix. The column headings at the top are called tactics. The tactic is a goal that an attacker is trying to achieve. For each tactic, there is a set of techniques on how to achieve the goal.
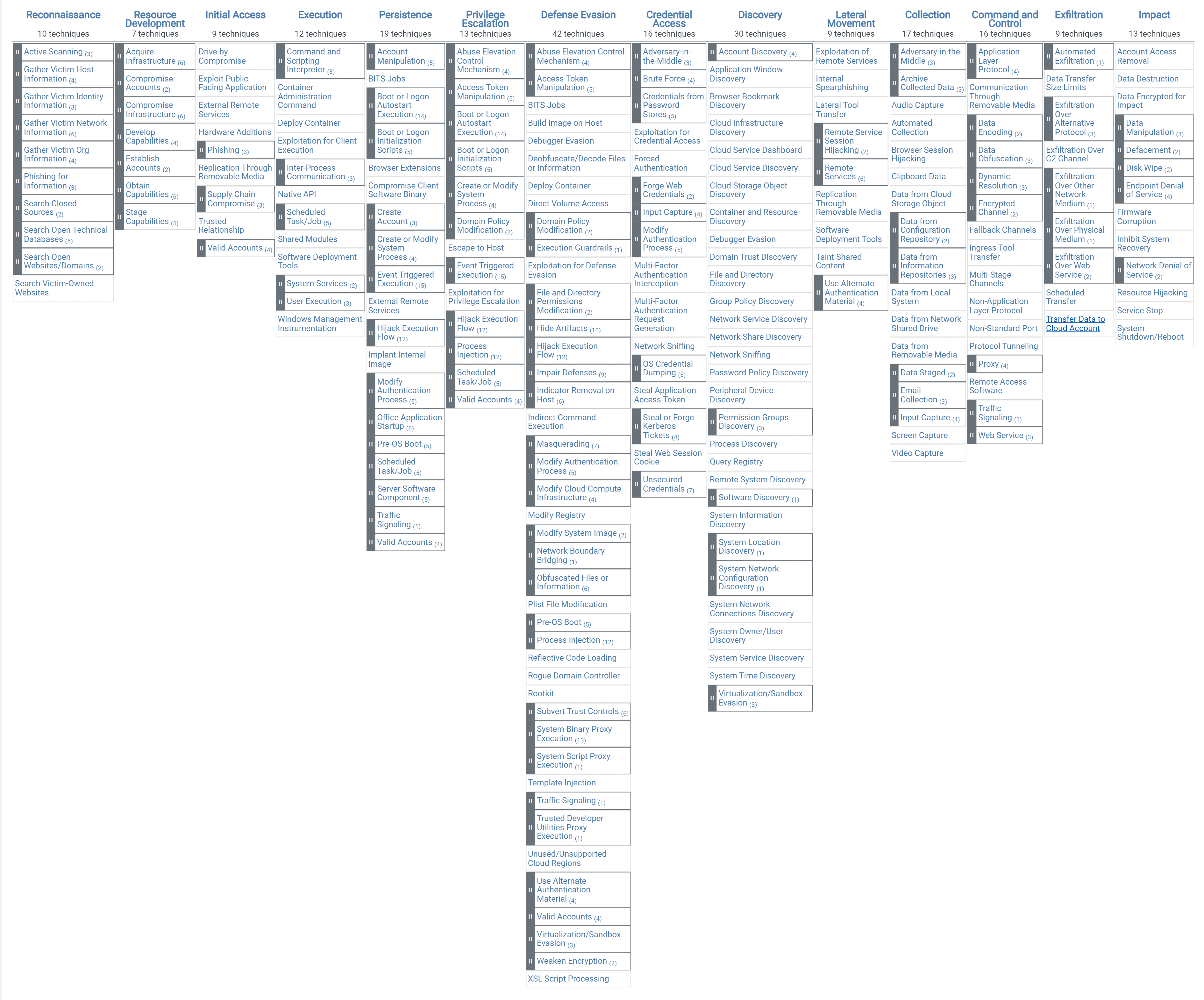
The ATT&CK Matrices: Enterprise, Mobile and ICS
MITRE has divided ATT&CK into three broad areas: Enterprise, Mobile and ICS. Each area has its own matrix.
The ATT&CK Enterprise Matrix
The complete ATT&CK Enterprise matrix covers the areas of.
from.
The tactics, i.e. the column labels, can be roughly interpreted as a kind of cyber kill chain, although they do not have to be traversed linearly.
The PRE area, i.e. the activities preceding an attack, consist of:
Reconnaissance: This includes all activities with which interesting information about people, technology or network infrastructure of an organisation can be obtained.
Resource Development: Based on the collected information, suitable attack tools are developed and an IT infrastructure for the attack is set up. This may include phishing websites and a command & control infrastructure.
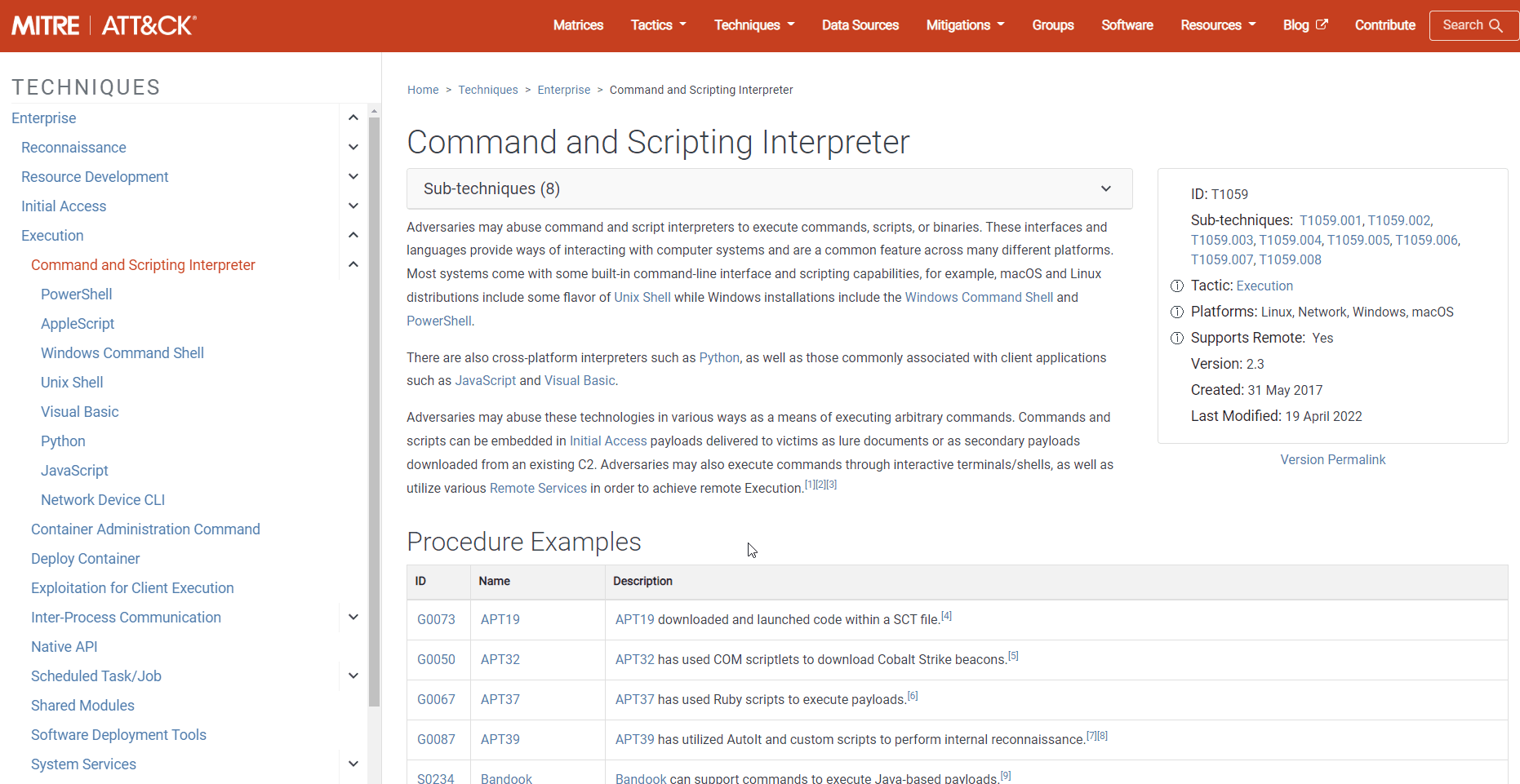
Example of an Enterprise ATT&CK technique.
For example, one of the tactics is Execution. In order for an attacker to successfully execute his own commands on an IT system, he will use one or more of the techniques listed in the Execution column.
One technique is the execution of code introduced by the attacker as a script with sub-techniques for execution as a Powershell script, CMD script (.BAT), and others. ATT&CK provides many details on each sub-technique and technique, including descriptions, examples, references, and suggestions for mitigation and detection.
How can ATT&CK specifically help businesses?
The MITRE ATT&CK framework is practical in a variety of situations. ATT&CK not only provides a comprehensive encyclopaedia for defenders of IT infrastructures (cyber defence), but also forms a basis for red teaming and penetration testing. This gives defenders (Blue Team) and Red Teamers a common taxonomy of behaviours of real attackers.
The most important use cases of MITRE ATT&CK for companies and public organisations include:
Simulation of attackers with ATT&CK.
A relevant question from a Blue Team perspective is often how well you are positioned against current attack techniques with the defence technologies you have in place. Testing techniques relevant to attackers in companies and organisations is certainly one of the most effective ways to:
The use of ATT&CK techniques by penetration testers increases the understanding of the results by their own IT security team.
Simulations can be designed to reflect techniques known to be used by certain relevant actors. This can be particularly useful when assessing how successful certain attackers can be against the controls in place in the environment.
Software tools for simulating attackers.
There are also software tools for testing certain techniques directly in one's own IT environment and which are also already aligned with the MITRE ATT&CK framework.
As always, caution is advised when performing attack simulations and cooperation with experienced penetration testers is recommended.
The work with these tools basically consists of three phases.
- Simulation: A selection of simulation criteria is made based on the desired tests. Dana either the software tool or a tester manually executes the selected technique.
- Review & Hunt: Examine the logs of all security tools and other preventive and detective deployed software on the IT systems. If the desired detection performance does not match the observation, this is also documented.
- Learn & Improve: Based on the results, it is checked whether an improvement of the performance for the detection of undesired activities is necessary. It should be taken into account that not all attack patterns or must always be prevented. It is usually sufficient if enough trip wires are designed.
ATT&CK- Resources
The MITRE ATT&CK framework is a very comprehensive tool to better understand the behaviour of attackers and also to secure one's own IT infrastructure against them. There is now a vast amount of valuable information and software tools available. The following is a briefly commented list - in addition to the software tools for attack simulation listed in the previous section.
MITRE Cyber Analytics Repository (CAR): While the ATT&CK framework focuses primarily on the description of threats and their activities, another MITRE project is concerned with the detection of threats: the Cyber Analytics Repository (CAR).
Inhalt
Releated Content

What is data security? Standards & Technologies
Data security is an important topic for all companies and authorities. Learn more about threats, measures and the legal framework here.
Read more...
Authentication: Differences to authorisation
Authentication and authorization are two words used in IT-Security. They might sound similar but are completely different from each other....
Read more...
Attack Vector and Attack Surface)
An attack vector is a way for attackers to penetrate a network or IT system. Typical attack vectors include ...,
Read more...
Buffer Overflow
A buffer overflow is a programming error that can be exploited by hackers to gain unauthorized access to IT systems. It is one of the best-known...
Read more...
Cybersecurity concept in 8 steps
A cybersecurity security concept refers to guidelines that are intended to ensure IT security in the company. It is about ensuring the availability,...
Read more...
Proxy Server
A proxy server works as an intermediary between two IT systems. Proxy servers offer different functionalities, improved security and optimised data...
Read more...
Endpoint Security
A proxy server works as an intermediary between two IT systems. Proxy servers offer different functionalities, improved security and optimised data...
Read more...
Need to Know Principle
The need-to-know principle describes a security objective for confidential information. Access should only be granted to a user if the information is...
Read more...
Top 10 Vulnerability Scanners for 2025
Vulnerability scanners are automated tools that organisations can use to monitor their networks, systems and applications for security weaknesses....
Read more...
NTLM Authentication
In this article, we explain what NTLM authentication is, how it works, and how it can be exploited by attackers.
Read more...
Information Security Management Systems (ISMS)
An Information Security Management System (ISMS) defines methods to ensure information security in an organisation.
Read more...
CVSS (Common Vulnerability Scoring System)
The CVSS Score provides a numerical representation (0.0 to 10.0) of the severity of a security vulnerability in IT. We explain how the Common...
Read more...
What is Information Security?
Information security is intended to ensure the confidentiality, integrity and availability of information. The information can be available on IT...
Read more...
CIS Controls - A Quick Overview of CIS Controls
The CIS Critical Security Controls (CIS Controls) are a prioritized list of protective measures to defend against the most common cyber attacks on IT...
Read more...
Penetration Tester Career Guide
How does one actually become a pentester? What does a pentester earn? Do career changers also have a chance? And what does a penetration tester do all...
Read more...
Firewalls & Firewall-Architecture
How does a firewall actually work? What does a good enterprise firewall architecture look like? To what extent does appropriate network segmentation...
Read more...Have we sparked your interest?
Just give us a call or write us a message!