The most important facts in brief
Beitrag teilen
Reading time 12 minutes
1 What is an IT security concept?
An IT security concept is an essential tool for companies to define basic measures for IT security and information security. Well-organised information security reduces the number of exploitable vulnerabilities in the information technology used and limits the impact in the event of a hacker attack.
The IT security concept does not specify how exactly these measures are to be implemented.
For example, the concept could specify that access to the internal network must be protected with VPN and two-factor authentication. However, no technical details such as specific software, hardware or cloud services are specified.
The IT security concept thus provides binding rules on how to implement IT security and the requirements of data protection in the company in order to maintain the protection goals of information security confidentiality, integrity and availability. The result is a concrete planning, management and implementation framework for IT security in the company.
An essential aspect of an IT security concept is its holistic approach: instead of concentrating on individual concrete solutions, the IT landscape of the company is considered as a whole.
2 How do I use this guide?
In this guide I show you how to create an IT security concept for an organisation. We highlight relevant issues, examine best practices and look at samples of the content of an IT security concept.
3 Goals of an IT security concept
The IT security concept is primarily concerned with protecting information from threat and loss. This can include, for example, confidential internal company data, customer data or personal data.
Suitable technical and organisational measures (TOM) are defined for this purpose.
Protection against hacker attacks
A hacker attack is an attempt by someone to gain unauthorised access to a computer, a computer system or a computer network with the intention of causing damage. These attacks aim to
An IT security concept should therefore definitely include measures to effectively prevent current attack scenarios such as ransomware.
Protection against insider attacks
However, an IT security concept should not only protect against hacker attacks from the outside. Internal employees also pose a great risk to the information security of companies. Careless employees or malicious (former) employees can steal or even delete data for financial or personal reasons.
External contractors and other third parties also often have legitimate access to sensitive data in order to work efficiently and flexibly. This poses a challenge for the IT security team. It is much more difficult to detect threats when the person in question already has legitimate access to sensitive information. Policies and technology can significantly reduce the risk of such data loss or theft.
Customer Requirements, Cyber Risk Insurance
A prudently created and carefully implemented IT security concept fulfils requirements with regard to.
Data protection, KRITIS and other legal requirements
An IT security concept ensures that the measures indispensable for data protection in accordance with the DSGVO are implemented.
According to §8a BSIG, operators of critical infrastructures (KRITIS) must prove that their IT security is state of the art. An IT security concept is mandatory for this purpose.
4 Procedure for creating an IT security concept
There are many different approaches to the creation of an IT security concept. The following steps are roughly based on the recommendations of BSI Standard 200-2 (IT-Grundschutz methodology).
- Definition of the information network: At the beginning of this IT security concept is the definition of which areas and locations of the company or authority are covered (definition of the scope).
- Structural analysis: A good knowledge of the information, process and technical support systems is an important basis for the IT security concept. In particular, information on all specialist and IT applications, IT systems and servers, networks, rooms and buildings must be compiled.
- Determining the need for protection: When determining the need for protection, the need for protection for the business processes, the information processed in the processes and the technical systems is determined. The protection requirement (e.g. normal, high, very high) and the security objectives (confidentiality, integrity, availability) are to be determined together with the persons responsible for the business.
- Apart from the need for protection of the data for one's own company or authority, the extent to which contractual or regulatory requirements may influence the need for protection or the measures to be defined must be examined. These can be requirements for the use of cryptographic methods for the implementation of the GDPR or contractual obligations to achieve certification maturity of the TISAX standard.
- Risk analysis and catalogue of measures Minimum requirements in the form of measures are assigned for all resources compiled in the structural analysis on the basis of the identified need for protection. The building blocks of the BSI Basic Protection can serve as support.
- IT security check: After defining the measures, the current status of implementation must be checked. Deviations and open points must be noted and an implementation strategy derived.
- Dealing with residual risks: It is likely that not all desired measures will be implemented immediately and completely. The currently remaining and identified residual risks should be dealt with responsibly.
- Updating and updating: Decisions should be made on the regular updating and control of the defined measures.
5 IT security concept sample/template
The structure and also the content of an IT security concept can be closely based on the procedure described in section 5.
5.1 Introductory chapters
As with any more comprehensive document, introductory chapters should at least provide information on the following factors.
5.2 Information network
A brief overview of the information network (organisations, institutions and companies) is given here. An overview presents the tasks as well as the competences and responsibilities. In the case of companies with several locations, a delimitation to individual locations or the head office is made, if necessary.
5.3 IT system architecture
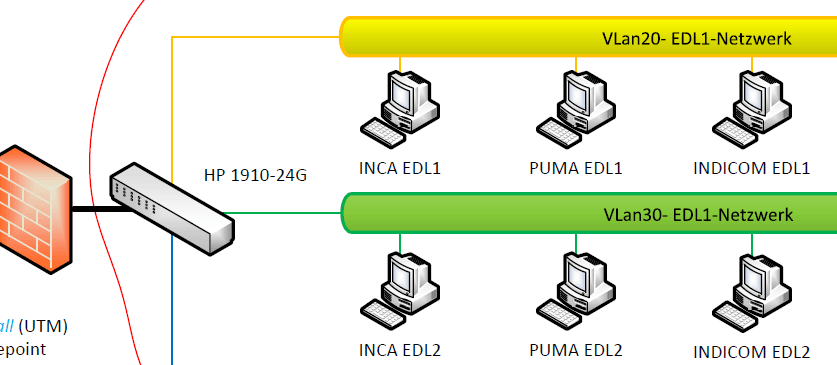
Networking and network
From a technical point of view, a network plan with servers, clients, VLANS, network components, network connections (both internally and between geographically separated locations) provides an overview of the information network under consideration. VPN endpoint and the now very relevant case of home office use are also included.
Example network diagram (detail)
IT infrastructure and servers
A list of all existing IT applications and IT systems (client, server, network components, etc.) is included here. Cloud-based applications with a reference to the cloud provider can also be part of the list.
Example List of IT Applications
| No. | Designation | Product/Details | Target group |
|---|---|---|---|
| A01 | Office Communication | MS Office 365 | All |
| A02 | Outlook | All | |
| A03 | Communication/Meetings | Microsoft Teams (SaaS) | All |
| A04 | HR Data Processing | Office / Excel | HR Team |
| ... | |||
| A50 | CAD/Planning | AutoCad | Project work |
| ... |
5.4 Determining the need for protection
In a protection needs assessment, the protection needed for the information used in the IT applications is determined. It should be noted that large companies can sometimes cope with damage more easily than small ones, public authorities often give different weighting to compliance with legal regulations than commercial enterprises, start-ups are more willing to take risks than established companies, etc.
Need for protection of IT applications
Based on the tasks for which an IT application is used, the need for protection in terms of confidentiality, integrity and availability must be assessed. The Damage categories and damage scenarios of the BSI can be used for this purpose.
Example of the need for protection of IT applications for personnel data processing
| Damage Scenario | Confidentiality | Integrity | Availability |
|---|---|---|---|
| Financial impact | high | normal | high |
| Violations of laws, regulations or contracts | high | high | normal |
| Impairments of the right to informational self-determination | high | normal | normal |
| Impairments of personal integrity | normal | normal | normal |
| impairment of the performance of duties | normal | high | normal |
| negative external impact | high | high | high |
| overall evaluation | high | high | high |
(Derived) protection requirement for IT systems
The protection requirement of an IT system is derived directly from the protection requirement of the IT application(s) processed on the IT system. According to the maximum principle, IT systems inherit the maximum of the protection requirement of all IT applications. However, depending on the situation, there may be justified deviations in one direction or the other.
(Derived) protection requirement for communication links
Similar to IT systems, the protection requirement for communication links is derived from the protection requirement of the IT applications that need them.
(Derived) protection requirement for rooms and buildings
The protection requirement for rooms and buildings follows from the IT systems operated there, documents stored and data carriers.
5.5 Observance of further requirements
The necessary protection requirement and the resulting measures can mainly be derived from the information to be protected in the IT applications. However, there are sometimes additional requirements that arise from other directions. These can be, for example:
If further requirements need to be implemented, this must be checked for each IT application and the requirements documented.
5.6 Action plan and risk analysis
The BSI recommends using the IT-Grundschutz-Bausteine for the measures to be implemented.
Example ISMS: Security Management
| Building Block | Relevance | Target Object | Justification |
|---|---|---|---|
| ISMS.1 Security Management | yes | Information Network |
Example ORP: Organization and Personnel
| Module | Relevance | Target object | Justification |
|---|---|---|---|
| ORP.1 Organisation | yes | Information network | |
| ORP.2 Personnel | Yes | Information network | |
| ORP.3 Information security awareness and training | Yes | Information network | |
| ORP.4 Identity and authorization management | Yes | Information network | |
| ORP.5 Compliance management (requirements management) | No | Being organised elsewhere |
Example SYS: IT Systems
| Module | Relevance | Target object | Justification |
|---|---|---|---|
| SYS.1.1 General Server | yes | S01, S03 | |
| SYS.1.2 Windows Server 2012 | no | ||
| SYS.1.3 Server on Linux and Unix | no | ||
| SYS.1.5 Virtualisation | yes | S02 (vSphere) | |
| SYS.1.6 Containerisation | yes | Cloud01 (Kubernetes Cluster at AWS) | |
| SYS.1.7 IBM Z | no | ||
| SYS.1.8 Storage Solutions | yes | NAS01 | |
| SYS.2.1 General Client | yes | CXXX | |
| SYS.2.2 Clients on Windows 8.1 | no | ||
| SYS.2.2.3 Clients on Windows 10 | yes | CXX | |
| SYS.2.3 Clients on Linux and Unix | no | ||
| SYS.2.4 Clients under macOS | no | ||
| SYS.3.1 Laptops | yes | CXX | |
| SYS.3.2.1 General smartphones and tablets | no | ||
| SYS.3.2.2 Mobile Device Management (MDM) | yes | [BYOD] | BYOD only, no organisation-owned smartphones |
| SYS.3.2.3 iOS (for Enterprise) | yes | (BYOD) | BYOD per MDM |
| SYS.3.2.4 Android | yes | (BYOD) | BYOD via MDM |
| SYS.3.3 Mobile Phone | mandatory | Information Network | |
| SYS.4.1 Printers, copiers and multifunction devices | yes | PR01, PR02, PR03 | |
| SYS.4.3 Embedded Systems | no | Information Network | |
| SYS.4.4 General IoT Device | no | Information Network | |
| SYS.4.5 Removable media | yes | all mobile media and USB sticks | no full inventory yet |
Other building blocks with measures to be examined are as follows:
If the measure situation is not sufficient (according to BSI standard requirements in our example), a further risk analysis must be carried out in order to expand the protection concept.
5.7 Implementation status of the action plan
Using a target/actual comparison, the current status of IT security can be determined quite easily at the organisational level.
Action plan <= Target/actual comparison => Measures implemented
The result is a list of deficient measures that still require implementation.
6 Risk analysis
The basic approach of the IT-Grundschutz of the Federal Office for Information Security (BSI) does not provide for a direct risk analysis. For the implementation of standard security measures, it is usually sufficient to apply the measures described in the BSI's basic security standards and catalogues of measures. This covers the general risks associated with the technology application.
If an IT system or application requires special protection or the risks are not described in the BSI standard documents, BSI Standard 100-3 describes a risk analysis based on IT-Grundschutz. However, there are also other procedures, for example according to ISO 27005 or other norms and standards.
A risk analysis should also be used if security requirements have been tightened or if IT systems are used in scenarios that are not provided for in the IT-Grundschutz list.
In the case of normal protection requirements, this may possibly be the case for new technologies. For example, until recently, the BSI had no standard measures for the use of Kubernetes. A separate risk assessment may also make sense when using cloud technologies (IaaS/PaaS/SaaS).
If a risk analysis is necessary, it is often advisable for the responsible business and technical managers and external security experts to work together. In particular, external consultants can contribute an attack-oriented perspective that is often not available internally.
7 What legal requirements does the DSGVO (Germany) place on an IT security concept?
Even in the DSGVO (General Data Protection Regulation, Germany), which applies to data protection in the EU, an IT security concept is not formally required.
8 How does an ISMS differ from an IT security concept?
An Information Security Management System (ISMS) is the big umbrella for all processes taking place and to be controlled within the framework of information security in a company or an authority. An IT security concept is usually a component of an ISMS.
An IT security concept focuses on the protection of data and information processed in information technology.
The ISMS is responsible, for example, for the continuation and ongoing updating of the IT security concept and the way in which residual risks are dealt with. The responsibilities and accountability are also regulated - in other words, the entire PDCA cycle.
In the case of an audit or certification (for example according to ISO/IEC 27001 or TISAX), the ISMS is primarily checked.
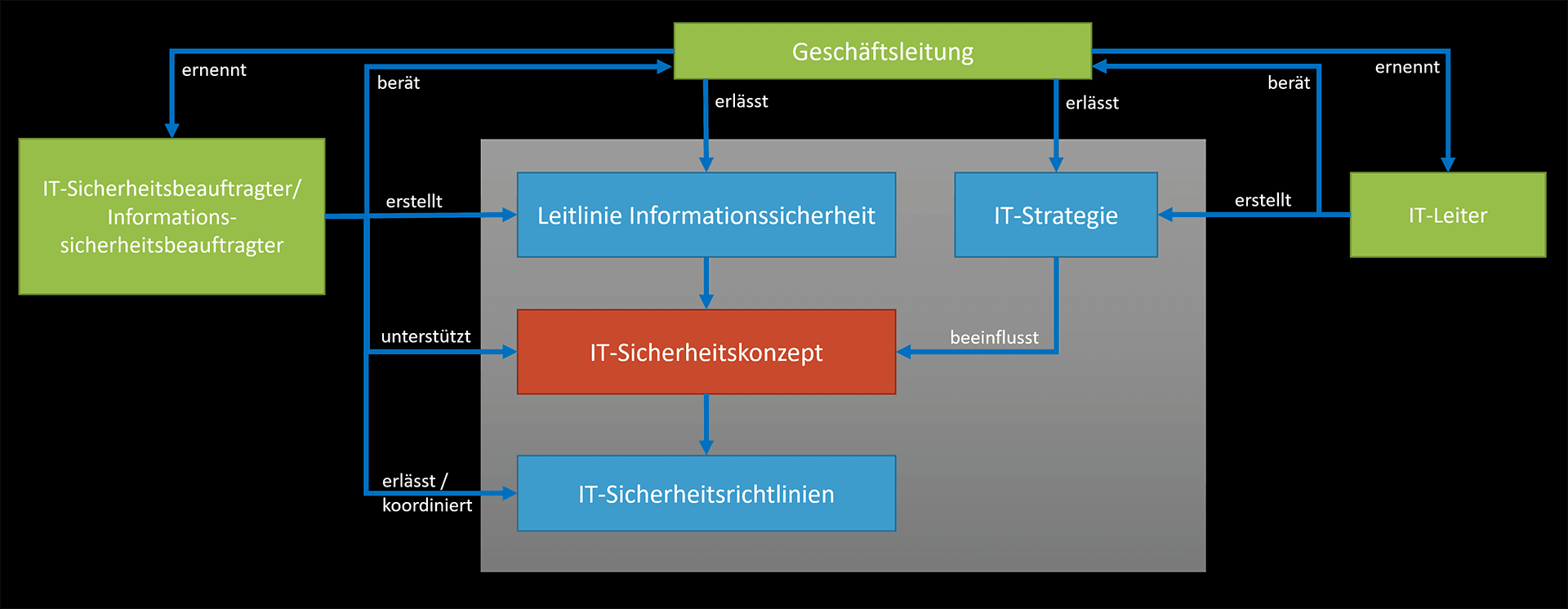
9 Who draws up the IT security concept?
The concrete procedure is specified by the IT security officer. Support is provided by the heads of the specialist departments and the administrative staff. But be careful, because creating an IT security concept requires extensive knowledge that no one can acquire in a short time.
Often, specialists are needed for the comprehensive identification of risks and the derivation of effective and cost-efficient measures, who are specifically hired in the company. However, such IT security specialists are often hard to find and have high salaries, which is why they are usually found in large companies.
For the creation of an IT security concept in SMEs (small and medium-sized enterprises), external consultants are often used, also because such a solution is usually much more cost-effective in the medium and long term.
Frequently asked questions
What is the scope of an IT security concept?
The information network of the IT security concept corresponds to the scope. Depending on the desired orientation, this can be very different. The scope can be the entire company with one or more locations. However, there are also other design options.
If external certification is desired, it is advisable to coordinate the information network with an experienced consultant at an early stage.
Inhalt
Releated Content

What is data security? Standards & Technologies
Data security is an important topic for all companies and authorities. Learn more about threats, measures and the legal framework here.
Read more...
Authentication: Differences to authorisation
Authentication and authorization are two words used in IT-Security. They might sound similar but are completely different from each other....
Read more...
Attack Vector and Attack Surface)
An attack vector is a way for attackers to penetrate a network or IT system. Typical attack vectors include ...,
Read more...
Buffer Overflow
A buffer overflow is a programming error that can be exploited by hackers to gain unauthorized access to IT systems. It is one of the best-known...
Read more...
Proxy Server
A proxy server works as an intermediary between two IT systems. Proxy servers offer different functionalities, improved security and optimised data...
Read more...
What is MITRE ATT&CK?
The MITRE ATT&CK Framework is a continuously updated knowledge base consisting of cyber attacker tactics and techniques across the attack lifecycle.
Read more...
Endpoint Security
A proxy server works as an intermediary between two IT systems. Proxy servers offer different functionalities, improved security and optimised data...
Read more...
Need to Know Principle
The need-to-know principle describes a security objective for confidential information. Access should only be granted to a user if the information is...
Read more...
Top 10 Vulnerability Scanners for 2026
Vulnerability scanners are automated tools that organisations can use to monitor their networks, systems and applications for security weaknesses....
Read more...
NTLM Authentication
In this article, we explain what NTLM authentication is, how it works, and how it can be exploited by attackers.
Read more...
Information Security Management Systems (ISMS)
An Information Security Management System (ISMS) defines methods to ensure information security in an organisation.
Read more...
CVSS (Common Vulnerability Scoring System)
The CVSS Score provides a numerical representation (0.0 to 10.0) of the severity of a security vulnerability in IT. We explain how the Common...
Read more...
What is Information Security?
Information security is intended to ensure the confidentiality, integrity and availability of information. The information can be available on IT...
Read more...
CIS Controls - A Quick Overview of CIS Controls
The CIS Critical Security Controls (CIS Controls) are a prioritized list of protective measures to defend against the most common cyber attacks on IT...
Read more...
Penetration Tester Career Guide
How does one actually become a pentester? What does a pentester earn? Do career changers also have a chance? And what does a penetration tester do all...
Read more...
Firewalls & Firewall-Architecture
How does a firewall actually work? What does a good enterprise firewall architecture look like? To what extent does appropriate network segmentation...
Read more...Have we sparked your interest?
Just give us a call or write us a message!