The most important in a nutshell
What is a firewall?
A firewall is a network security system that creates a barrier between two networks. It is used to monitor and control incoming and outgoing traffic to prevent unauthorized access to computers and networks.
By comparison, a "real fire wall" is understood to be a physical barrier to slow the spread of forest fires until responders can extinguish them. Similarly, firewalls limit the spread of cyber threats until IT security teams can address them.
Firewalls use a set of preconfigured rules known as firewall security policies to determine how to detect and block unwanted traffic.
Firewall rules check the control information of data packets or the data packets themselves (DPI - Deep Packet Inspection) and then allow or block them according to criteria set by IT or security administrators. These rules are critical to how a firewall protects the network from intruders, and managing them correctly is critical to network security.
Host-based firewalls and network-based firewalls
A network-based firewall secures an entire computer network by filtering incoming and outgoing traffic to the secured LAN. Such firewalls often consist of hardware and provide a more robust defensive barrier than host-based firewalls.
Host-based firewalls, on the other hand, prevent unauthorized data traffic on individual devices - known as hosts - and are software-based. An excellent example of a host-based firewall is the Windows firewall, which is installed by default on all Windows systems.
SOHO firewalls
In a typical home network with smartphones, baby monitors, video doorbells and other smart devices, the basic firewall in the WLAN router or modem connected to the ISP is usually the only firewall used in a home or SOHO network.
However, to increase the security and functionality of such a network, there are also special hardware firewalls.
Firewalls for enterprises
Enterprise firewalls improve the security posture by providing visibility into users, devices, applications and threats on the network. These firewalls provide prioritized alerts and can prevent most viruses and worms transmitted over the network. Additional features of enterprise firewalls include preventing the transmission of unwanted or offensive content and protecting against unauthorized remote access. Many firewalls can operate as VPN gateways to specifically allow and control external access.
Why do I need a firewall?
Firewalls are one of the fundamental building blocks of enterprise IT security. A firewall is the first line of defense against threat actors attempting to disrupt business operations, compromise corporate data, or commit theft for financial gain.
A firewall can block attacks from external sources
The main function is to restrict unauthorized access from external IP addresses. Depending on the type and filtering that a firewall can apply, most direct attacks can be blocked.
For example, a Web Application Wifewall (WAF) can pre-scan URLs for SQL injection attacks (SQLi) or log4j attack patterns.
A firewall can block traffic from internal to external
A firewall can block traffic originating from internal systems to external destinations. For example, a firewall might block access to known malicious IP addresses to block command-and-control (C2) traffic or websites with malware.
The ability of firewalls to act as a tool to weed out unwanted traffic also helps organize data efficiently and implement data leak prevention (DLP) concepts. For example, shadow IT applications can lead to data breaches when employees use a cloud-based data-sharing application outside the purview of the corporate IT department, such as a private OneDrive account.
A firewall can block internal traffic to protect against insider threats
Insider threats are another critical challenge that firewalls can help address. Suppose someone has compromised a system and is working on a deeper infiltration of the network. If there are no internal firewalls, an attacker could quickly jump from one compromised client to the next, then perhaps to a vulnerable server and finally to the domain controller. Internal firewalls often prevent such situations, which can lead to a complete compromise of the LAN.
How does a firewall work?
A firewall forms a boundary between an untrusted network and the network it protects. It inspects all packets entering and leaving the network. Firewalls examine data and use a set of preconfigured rules to distinguish between benign and malicious packets. Different firewalls use different means to inspect data packets for malicious code. These include packet filtering firewalls, stateful inspection firewalls, proxy firewalls, and "next-generation firewalls" (NGFW). The filters sort out unwanted data packets, while the rest can be forwarded to the destination.
The rules can be based on various aspects derived from the packet information, e.g. source IP, destination IP, the connection status or even the content (in this case often called DPI, Deep Packet Inspection).
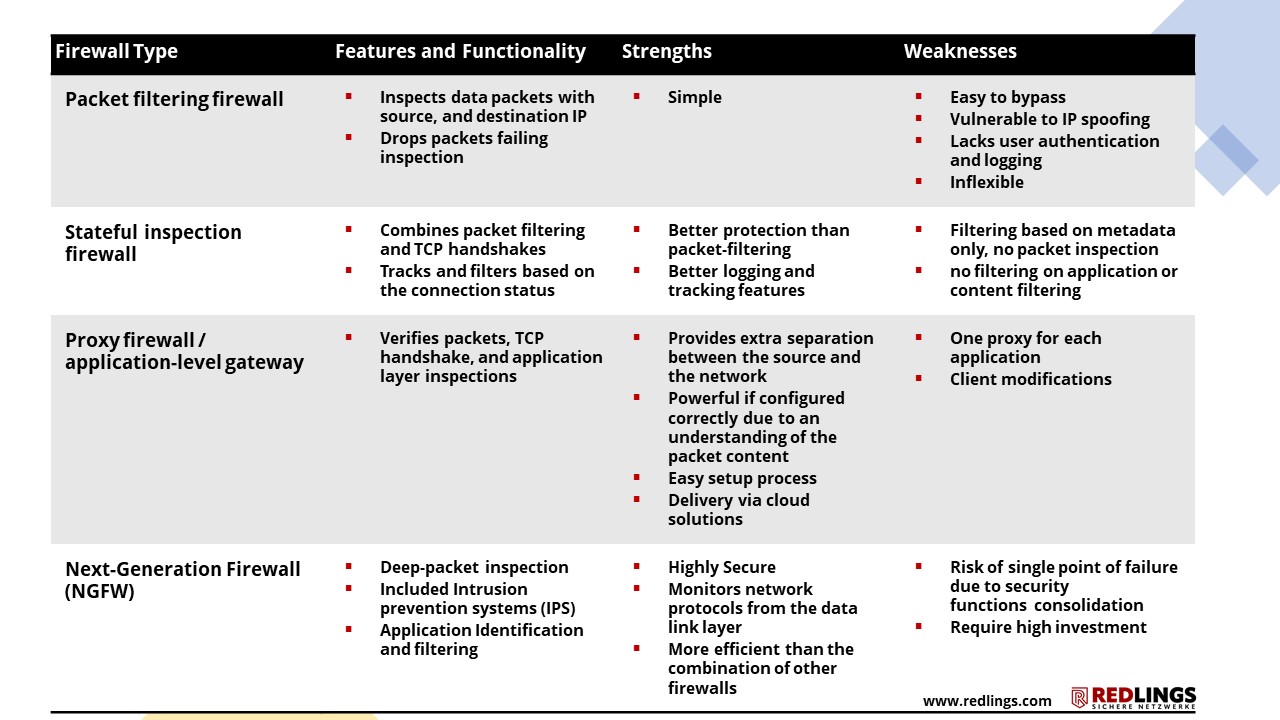
Firewall types by filtering method (Packet Filtering Firewall, Stateful Inspection Firewall, Proxy Firewall, Next-Gen Girewall).
Packet filter firewall
A packet filter firewall restricts access to packets based on source and destination addresses or a specific transport protocol. The firewall looks for information in the IP, TCP, or UDP header before deciding whether to allow or deny the packet. A packet-filtering firewall examines packets in isolation and does not know the context of the packet.
This would allow a firewall to block traffic to known malicious external IPs. Pure packet filter firewalls are rarely used these days.
Stateful Inspection Firewall
A stateful inspection firewall uses state and context to monitor data packets. This is done by understanding connections between systems. This would allow a firewall to let external systems communicate with an internal system if the internal system initiated the connection. This is the standard use case for users accessing web servers with their browsers.
Proxy firewall
A proxy firewall filters traffic at the application layer to protect network resources. URL filtering takes place at this level. Proxy firewalls are also called application firewalls or gateway firewalls. The firewall acts as a mirror of the server, separating it from the Internet.
Attackers often need a direct connection to a computer to compromise it. Proxy firewalls prevent direct connections to the device from the Internet, making such attacks more difficult.
Next Generation Firewall (NGFW)
To be considered NGFW, a firewall must have features such as stateful inspection, intrusion prevention mechanisms, integration of CTI sources, application awareness to block unwanted applications, capabilities to defend against evolving threats, and the ability to integrate future information sources. Next-generation firewalls are typically fed threat information on an ongoing basis. They can perform stateful inspection and block application-level attacks and threats from more sophisticated malware.
Overview
The table below shows the differences between the various types of firewalls based on their key features, strengths and weaknesses:
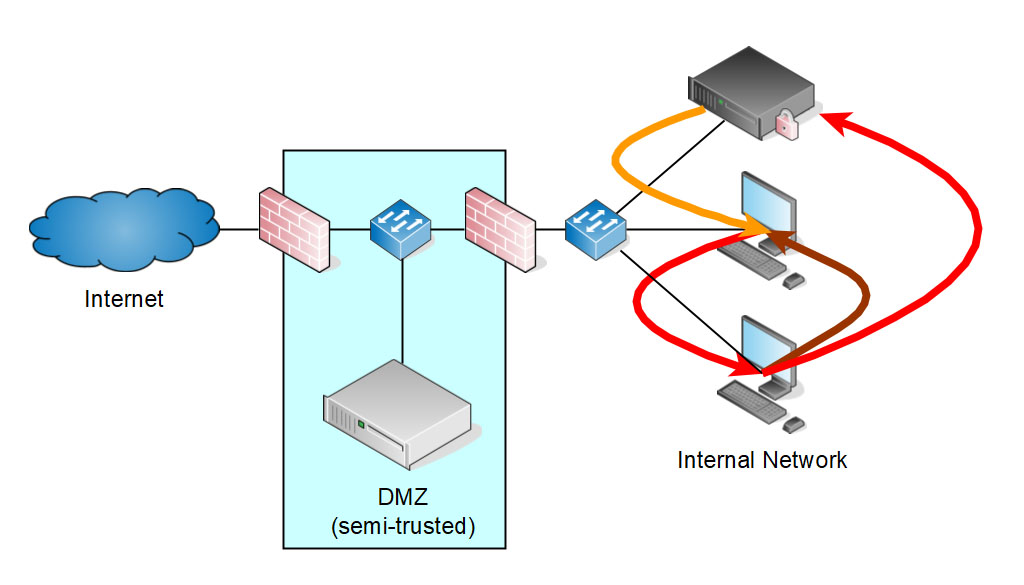
Lack of internal network segmentation - why do flat networks fail?
In a flat net, the classic perimeter defense is used. These networks can be described as hard from the outside but soft from the inside. They are little to no segmented, so users cannot be prevented from accessing certain parts of the network, which makes it easy for cyber attackers to access any system.
Flat computer networks are designed to minimize costs and management and maintenance efforts. However, these networks often fail catastrophically when confronted with modern threats.
Flat networks allow all systems and applications to interact, making it difficult to identify which connections and data flows are legitimate. Flat internal networks fail because they provide little or no internal filtering at the OSI Datalink, Network, and Transport layers. Such networks can allow an insider threat access to multiple critical systems.
Dividing a network into virtual LANs (VLANs) does not help against such threats.
Despite these issues, enterprises continue to use flat networks because they are easy to maintain and management of additional firewalls - beyond the perimeter firewall - is unnecessary.
How should a firewall segment a network?
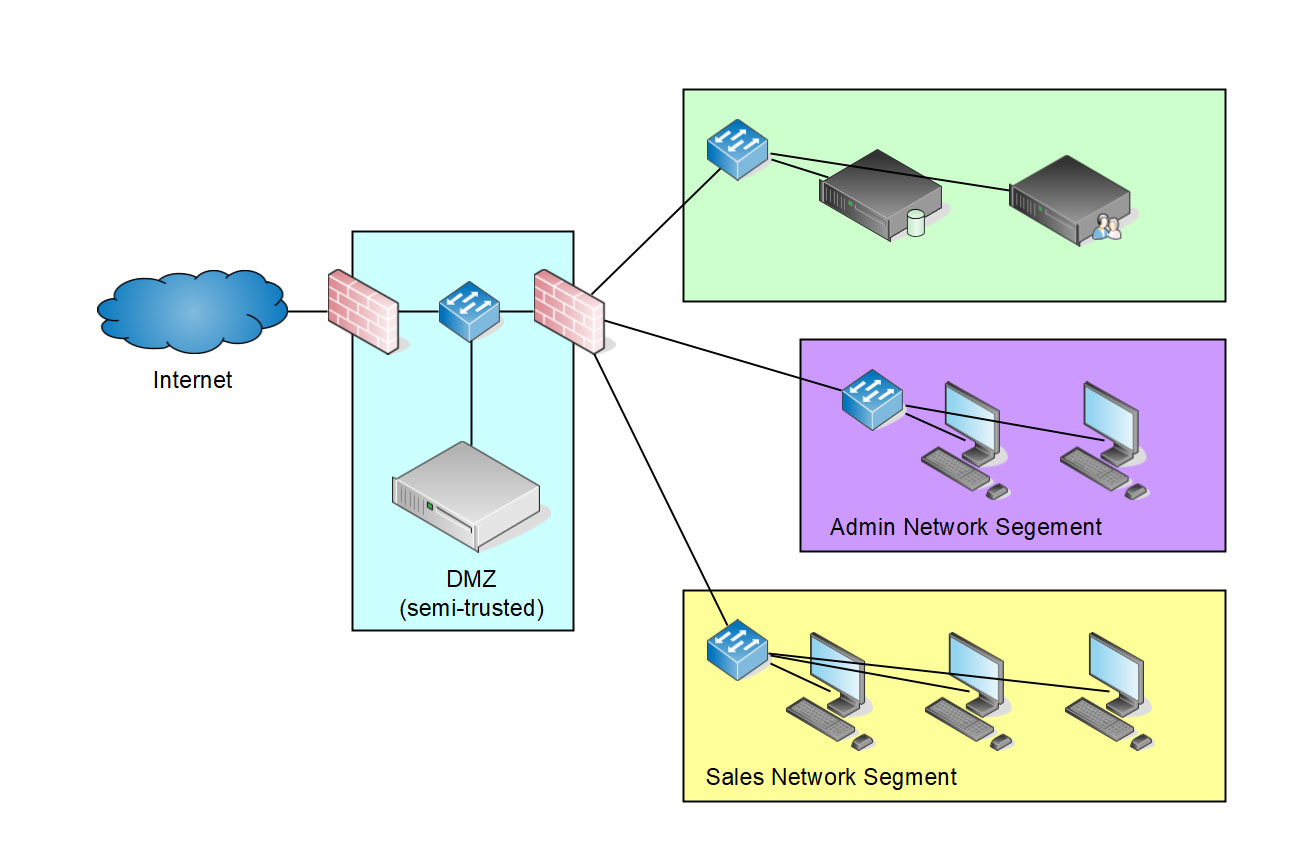
Segmentation involves dividing larger environments or networks into smaller parts or subnets, even down to the host itself. Segmenting a network is a way to better defend it by helping to make intrusion more difficult and - if it happens - to detect it early. Although firewalls prevent unauthorized traffic between segments, segmentation can increase management overhead and complexity.
Implementing appropriate segmentation is necessary to balance management efficiency and security requirements. Simple networks with no public services can use a two-tier configuration that includes the LAN and the Internet. In contrast, a simple network that provides limited public services can use a three-tier firewall configuration with ports for the Internet, a DMZ, and a trusted internal port.
Depending on the complexity of the network, additional ports can be added as needed. For example, segmentation of credit card processing systems is required for PCI DSS compliance. Further, the criticality of the systems must be considered. For example, it would make sense to put a domain controller or other critical servers in a different segment than the user workstations to reduce the direct attack surface.
Finally, segmentation should also take into account the relevant threat scenarios. For example, legacy systems that cannot be patched and industrial control systems (ICS) or SCADAs use open architectures with limited authentication/authorization when connecting to other systems. Such systems should always be isolated in separate segments.
Threats that firewalls are still no match for
Modern firewall architectures can defend against most threats. However, there are still certain situations where they can have problems. Deep packet filtering (DPI) can detect, block or redirect information packets, which simple packet filtering cannot. However, only proxy firewalls and NGFWs are capable of deep packet filtering.
Sophisticated cyberattacks can bypass the functions of proxy firewalls and NGFWs. Firewall bypass attacks manipulate packets so that a proxy/NGFW does not detect the threat. In addition, cryptography poses a challenge because it prevents almost all packet inspection methods due to the encryption used. A list of threats that firewalls have to contend with includes:
Malware
A packet filter firewall restricts access to packets based on source and destination addresses or a specific transport protocol. The firewall looks for information in the IP, TCP, or UDP header before deciding whether to allow or deny the packet. A packet-filtering firewall examines packets in isolation and does not know the context of the packet.
Firewalls can block traffic to known malicious IP addresses. Still, in some cases, it can be difficult to detect malware. These threats are complex and constantly evolving, and there is always the possibility that an attack will compromise denooch systems.
Insider threats and insider attacks
Although network segmentation by firewalls can limit the movement of insider threats and increase the likelihood of detection, it may not be enough to prevent intrusions. Intrusion detection systems, either installed as a dedicated IDS or integrated into a next-generation firewall, can help detect such malicious activity. Insider threats, however, remain a constant challenge.
Distributed Denial of Service (DDoS) attack
In a distributed denial of service (DDoS) attack, a network is flooded with so much traffic that it can no longer function normally. These attacks are particularly difficult to deal with because they overload the firewall. To protect against DDoS attacks, special DDoS protection services from SaaS companies may be required, as they can handle huge traffic loads.
Open source firewalls and free firewalls
Organizations and individuals can use high-quality free and open-source firewalls. These are especially useful for new organizations that have tight budgets. Similar to some commercial systems, some of some of these firewalls can also be run as virtual machines. Below is a list of examples of such firewalls:
Commercial firewalls and hardware firewalls
Commercial firewalls and hardware firewalls are recommended for mature businesses with many users that require a strong security posture. Examples of these firewalls are:
- CISCO Firepower (derived from pfSense, very powerful firewall)
- Fortinet FortiGate (firewall distribution based on FreeBSD and the packet filter pf)
- Palo AltoNetworks NGFW (as part of the Linux kernel)
- JuniperNetworks NGFW (commercial firewall, but free version available)
For some commercial firewalls, a software version is available that can be deployed as a virtual machine.
Host-based software firewalls (personal firewalls)
Personal firewalls can provide security on individual devices. Examples include:
- Microsoft Defender Firewall (part of Windows and Windows Server operating systems)
- Avast Premium Security
- Bitdefender Total Security
- Comodo Internet Security
- Norton 360 Premium
For some commercial firewalls, a software version is available that can be deployed as a virtual machine.
Cloud-based firewalls
These firewalls form a virtual barrier and can help protect the cloud infrastructure. These include:
Security Policies for Firewalls - How to secure a firewall?
Firewalls are only as secure as their configuration. Security policies for firewalls are rules that are used to secure networks. The network administrator configures them to determine what traffic is allowed to pass through the firewall and what traffic is to be prohibited.
The core components of a firewall security policy are the actions and the corresponding conditions. When the firewall receives a data packet, it compares it to the conditions in the security policy. If a packet meets a condition, it is processed according to the "actions" specified in the policy.
The default policy is one of the most important considerations to make when setting up a firewall. It determines what happens when no other rules match the traffic.By default, a firewall can either allow or block any traffic that does not match the previous rules.
However, the default rule should always be to block traffic that does not match any other rule.
Security testing and penetration testing of firewalls
Firewall security testing depends on the type of service a firewall provides. For example, testing a simple stateful inspection firewall is different from testing an advanced next-generation firewall (NGFW) that has integrated intrusion detection and prevention (IDS/IPS) capabilities while also enforcing internal network segmentation.
One of the most common methods is firewall penetration testing. Such a pentest focuses on identifying firewall-related configuration errors and vulnerabilities.
Content
Releated Content

What is data security? Standards & Technologies
Data security is an important topic for all companies and authorities. Learn more about threats, measures and the legal framework here.
Read more...
Authentication: Differences to authorisation
Authentication and authorization are two words used in IT-Security. They might sound similar but are completely different from each other....
Read more...
Attack Vector and Attack Surface)
An attack vector is a way for attackers to penetrate a network or IT system. Typical attack vectors include ...,
Read more...
Buffer Overflow
A buffer overflow is a programming error that can be exploited by hackers to gain unauthorized access to IT systems. It is one of the best-known...
Read more...
Cybersecurity concept in 8 steps
A cybersecurity security concept refers to guidelines that are intended to ensure IT security in the company. It is about ensuring the availability,...
Read more...
Proxy Server
A proxy server works as an intermediary between two IT systems. Proxy servers offer different functionalities, improved security and optimised data...
Read more...
What is MITRE ATT&CK?
The MITRE ATT&CK Framework is a continuously updated knowledge base consisting of cyber attacker tactics and techniques across the attack lifecycle.
Read more...
Endpoint Security
A proxy server works as an intermediary between two IT systems. Proxy servers offer different functionalities, improved security and optimised data...
Read more...
Need to Know Principle
The need-to-know principle describes a security objective for confidential information. Access should only be granted to a user if the information is...
Read more...
Top 10 Vulnerability Scanners for 2025
Vulnerability scanners are automated tools that organisations can use to monitor their networks, systems and applications for security weaknesses....
Read more...
NTLM Authentication
In this article, we explain what NTLM authentication is, how it works, and how it can be exploited by attackers.
Read more...
Information Security Management Systems (ISMS)
An Information Security Management System (ISMS) defines methods to ensure information security in an organisation.
Read more...
CVSS (Common Vulnerability Scoring System)
The CVSS Score provides a numerical representation (0.0 to 10.0) of the severity of a security vulnerability in IT. We explain how the Common...
Read more...
What is Information Security?
Information security is intended to ensure the confidentiality, integrity and availability of information. The information can be available on IT...
Read more...
CIS Controls - A Quick Overview of CIS Controls
The CIS Critical Security Controls (CIS Controls) are a prioritized list of protective measures to defend against the most common cyber attacks on IT...
Read more...
Penetration Tester Career Guide
How does one actually become a pentester? What does a pentester earn? Do career changers also have a chance? And what does a penetration tester do all...
Read more...Have we sparked your interest?
Just give us a call or write us a message!