Essentials in brief
Beitrag teilen
Reading time 7 minutes
1. What is an attack vector?
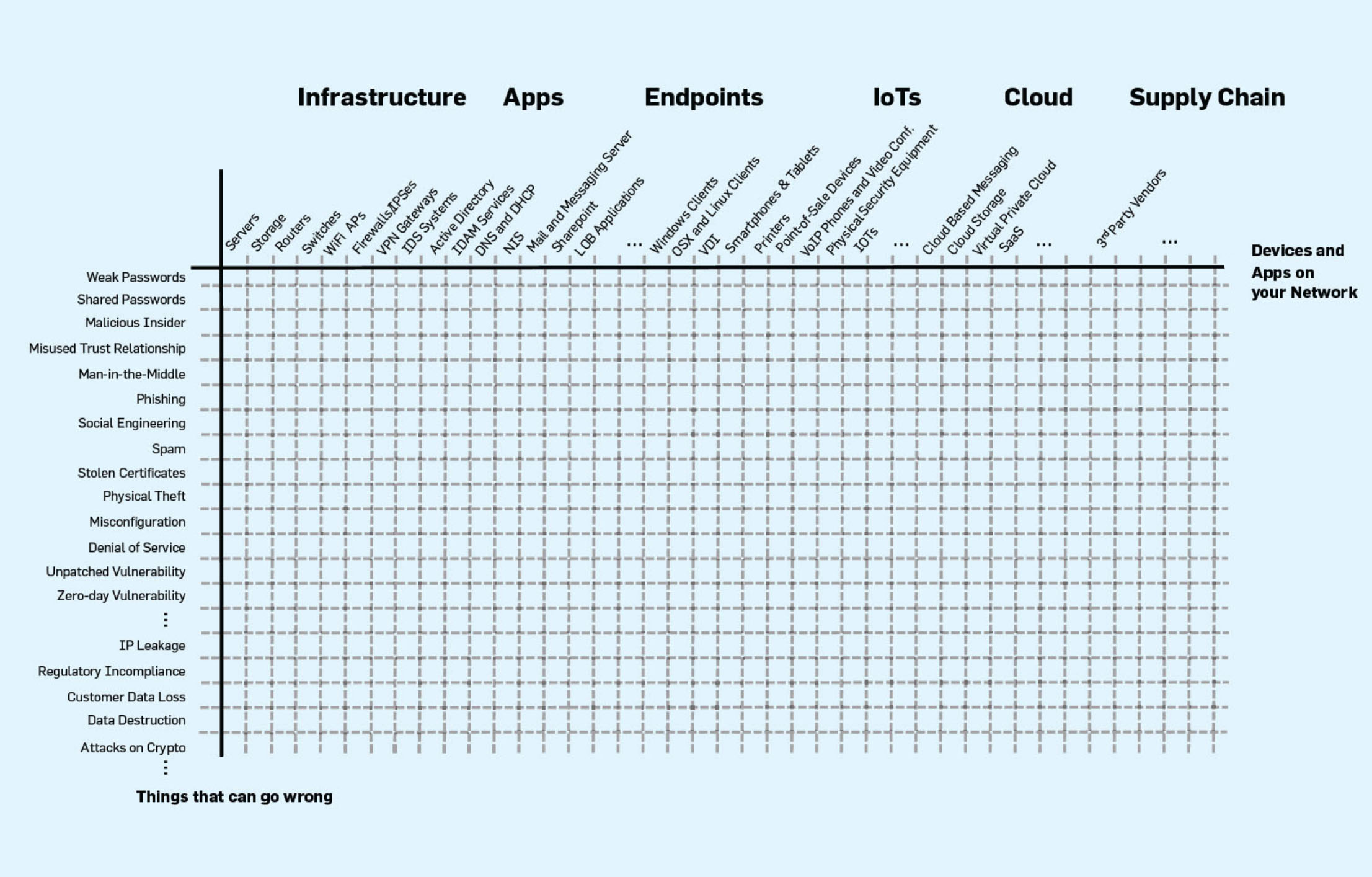
In IT security, an attack vector is a way or technique that an attacker uses to exploit a security vulnerability to attack a computer system or software component.
The sum of all attack vectors of an IT system is also called the attack surface. The more attack vectors an IT system offers, the larger its attack surface. And the larger the attack surface, the more options an attacker has to compromise the IT system - i.e. to manipulate, delete, steal or take control of data.
It is often necessary to exploit several attack vectors in succession or even simultaneously so that an attacker can achieve the desired goal.
Example: to steal data, an attacker can exploit the following attack vectors in sequence:
2. How are attack vectors exploited?
The basic procedure for exploiting attack vectors is often as follows:
- The cybercriminals identify a target system to penetrate or exploit.
- The cybercriminals use data collection and observation tools such as OSINT, emails, malware or even social engineering to gain more information about the target system.
- The cybercriminals use the information obtained to determine the attack surface with the target's attack vectors. This is then used to determine the best attack vectors and develop the tools to exploit them.
- Using the prepared tools, the security measures are breached and an inconspicuous malware is installed. This initial malware often does not yet contain any malicious function, but only makes contact with a central command & control server of the cybercriminals. Then this malware goes to "sleep" and waits for commands.
- After that, it begins to monitor the network, steal passwords and other access data via keyloggers, and transfer personal and financial data to the internet. In further steps, other computers further inside the network can also be infected. In this case, the initial computer is often even used as a communication proxy.
In the reverse - i.e. to protect attack vectors from being exploited - policies and processes must be put in place. This is to effectively prevent attackers, malicious hackers and criminals from finding information about attack vectors and exploiting them.
3. What is the role of attack vectors and the attack surface?
Depending on the goal an attacker wants to achieve, the examination of the attack surface plays a crucial role.
For a server that is not accessible from the internet, the attack surface is completely different from that of a public web server Also, the choice of means often differs depending on the attack target and the possible attack vectors as well as their evaluation with regard to the chances of success, the effort as well as the risk of being discovered.
Cybercriminals earn money by illegally attacking IT systems or the software services running on them in order to steal banking information, personal data, customer lists and company secrets. The targets are often corporate IT systems, such as employees' desktops. Attack vectors regularly include social engineering activities such as phishing.
However, some cybercriminals have developed other, more sophisticated, methods to monetise their attacks, such as compromising hundreds of thousands of IT systems to build a botnet to send spam, conduct covert cyberattacks, mine cryptocurrencies, or simply rent the botnet to other criminals for their purposes. With the large mass of IT systems, attack vectors that can be highly automated are interesting, such as scanning the internet for IoT devices with weak security configurations like default passwords that have not been changed. For example, the Mirai botnet has spread through IoT devices and default passwords accessible from the internet.
4.Typical attack vectors and examples.
Phishing for passwords
Username and password remain the most commonly used credentials. Compromised refers to these when they have become accessible to unauthorised persons. Phishing is a social engineering technique where an email/SMS/message has been sent to a person asking them to enter their login details on a fake website. The fake website then transmits the stolen access data to the attacker. Depending on the amount of preparation and "realism", this approach is unfortunately still quite effective today.
A very effective countermeasure to this attack vector is the use of two-factor authentication (2FA) for logins.
Exploiting misconfigurations
System configuration errors can be, for example, setup pages that have not been deactivated or users set up with default usernames and passwords. This can also include insufficient hardening of accessible IT systems, system services that have not been deactivated or a faulty firewall configuration. These misconfigurations represent an easy entry point for attackers to exploit.
Recent malware attacks such as Mirai (use of default passwords via SSH on IoT devices) illustrate this threat.
Countermeasures include sensible hardening rules. Penetration testing can also help in checking for such attack vectors.
Exploiting vulnerabilities in unpatched software
If an IT system, network device or application has an unpatched vulnerability, an attacker can exploit this to gain unauthorised access.
Since true zero-day attacks are very rare, an effective countermeasure is to apply all software patches and updates promptly.
Exploiting insider knowledge
Malicious or disgruntled employees can use their privileges to connect into networks and systems to obtain sensitive information such as customer lists (PII) and intellectual property (IP).
Countermeasures here are admittedly not that easy. However, implementing the "need-to-know" principle for granting access rights helps here because it ensures that each employee really only has access to the information that is necessary for the current activities. In this respect, at least the damage can be limited in such cases. In principle, UBA (User Behaviour Analytics) could also help to identify such cases, but in practice a clean implementation is quite challenging.
DDoS attacks
In DDoS attacks, victims are flooded with fake requests, rendering their IT system or network unusable. As a result, the services available there are no longer available to the legitimate recipients. These types of attacks often target the web servers of financial, commercial and government organisations.
The most important DDoS countermeasures are the use of a bandwidth-strong cloud provider that pre-filters the network traffic ("scrubbing centre"), the use of regionally distributed data centres and also own filtering measures, for example via a web application firewall (WAF).
Intrusion into buildings
In targeted attacks, attackers often use physical threat vectors to bypass strong digital controls. Since criminals count on IT security professionals to have invested the most effort in the cyber domain, targeted attacks often like to switch to bypassing physical security barriers such as doors/windows. This also includes social engineering techniques, for example, to fool the security team at the entrance gate into thinking they are a service employee or tradesman. Or an attacker may pose as a new employee and rely on a real employee to politely hold the door open for them as they enter the company building together.
5. How do I reduce the risk of attack vectors being exploited?
Criminals use a wide range of methods to penetrate corporate IT systems. Clearly, these methods are constantly evolving. The job of IT security and operations teams is to implement policies, tools and techniques that most effectively protect against these attacks. The following list is intended to highlight some effective protection mechanisms in this regard:
Inhalt
Releated Content

What is data security? Standards & Technologies
Data security is an important topic for all companies and authorities. Learn more about threats, measures and the legal framework here.
Read more...
Authentication: Differences to authorisation
Authentication and authorization are two words used in IT-Security. They might sound similar but are completely different from each other....
Read more...
Buffer Overflow
A buffer overflow is a programming error that can be exploited by hackers to gain unauthorized access to IT systems. It is one of the best-known...
Read more...
Cybersecurity concept in 8 steps
A cybersecurity security concept refers to guidelines that are intended to ensure IT security in the company. It is about ensuring the availability,...
Read more...
Proxy Server
A proxy server works as an intermediary between two IT systems. Proxy servers offer different functionalities, improved security and optimised data...
Read more...
What is MITRE ATT&CK?
The MITRE ATT&CK Framework is a continuously updated knowledge base consisting of cyber attacker tactics and techniques across the attack lifecycle.
Read more...
Endpoint Security
A proxy server works as an intermediary between two IT systems. Proxy servers offer different functionalities, improved security and optimised data...
Read more...
Need to Know Principle
The need-to-know principle describes a security objective for confidential information. Access should only be granted to a user if the information is...
Read more...
Top 10 Vulnerability Scanners for 2025
Vulnerability scanners are automated tools that organisations can use to monitor their networks, systems and applications for security weaknesses....
Read more...
NTLM Authentication
In this article, we explain what NTLM authentication is, how it works, and how it can be exploited by attackers.
Read more...
Information Security Management Systems (ISMS)
An Information Security Management System (ISMS) defines methods to ensure information security in an organisation.
Read more...
CVSS (Common Vulnerability Scoring System)
The CVSS Score provides a numerical representation (0.0 to 10.0) of the severity of a security vulnerability in IT. We explain how the Common...
Read more...
What is Information Security?
Information security is intended to ensure the confidentiality, integrity and availability of information. The information can be available on IT...
Read more...
CIS Controls - A Quick Overview of CIS Controls
The CIS Critical Security Controls (CIS Controls) are a prioritized list of protective measures to defend against the most common cyber attacks on IT...
Read more...
Penetration Tester Career Guide
How does one actually become a pentester? What does a pentester earn? Do career changers also have a chance? And what does a penetration tester do all...
Read more...
Firewalls & Firewall-Architecture
How does a firewall actually work? What does a good enterprise firewall architecture look like? To what extent does appropriate network segmentation...
Read more...Have we sparked your interest?
Just give us a call or write us a message!